Corporate Freeloading Makes Open Source Vulnerable

Published by The Lawfare Institute
in Cooperation With

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz.
Corporate Freeloading Makes Open Source Vulnerable
The foundations for open-source software security (OpenSSF) and for the promotion of JavaScript (OpenJS) have jointly warned the takeover of the XZ Utils project (a likely state-backed multiyear effort to subvert an open-source project by gaining the trust of the package’s maintainer) was probably not an isolated incident.
The foundations said that several “credible takeover attempts” had been unsuccessfully launched against JavaScript-related projects. Their post provides a list of “suspicious patterns” of behavior that could indicate an attempted social engineering attack. The list isn’t wrong, but to some degree it misses the point.
The “vulnerability” that makes open-source software susceptible to these sorts of social engineering attacks is baked into its “business model” of internet strangers collaborating to achieve a common goal.
Malicious actors don’t dupe their way into positions of responsibility within projects—they earn these positions of trust by behaving like good open-source citizens, contributing code and doing real work.
The behaviors that the post identifies as suspicious are what we’d call “complementary” tactics that increase pressure on open-source project maintainers but aren’t the main avenue of attack. These include, for example, “friendly yet aggressive and persistent pursuit of [a] maintainer … by relatively unknown members of the community” or “endorsement coming from other unknown members of the community who may also be using false identities, also known as ‘sock puppets.’”
The post spells out the key problem: “[M]any projects in the JavaScript ecosystem are maintained by small teams or single developers who are overwhelmed by commercial companies who depend on these community-led projects yet contribute very little back.”
The Cybersecurity and Infrastructure Security Agency (CISA), the U.S. cybersecurity authority, agrees. In a “Lessons from XZ Utils” post, it calls for technology companies that benefit from open-source software to become “sustainable contributors” to the open-source packages they depend on. Getting companies to contribute to open-source software, either with money, or by helping to maintain projects, would be a paradigm shift. But without these contributions, the ecosystem will remain vulnerable to malicious “good samaritan” attacks.
Sisense Loses a Bucketload of Keys, Feds Step In
Last week, CISA announced it was “collaborating with private industry partners to respond to a recent compromise discovered by independent security researchers impacting Sisense, a company that provides data analytics services.”
This is a potentially disastrous breach. Sisense holds a bucketload of credentials and secrets, which it uses to access customers’ data sources so that it can gather, analyze, and visualize that information on their behalf.
According to Krebs on Security, attackers obtained access to the company’s source code repository, which contained access details for Sisense’s Amazon S3 bucket. The attackers then used the “S3 access to copy and exfiltrate several terabytes worth of Sisense customer data, which apparently included millions of access tokens, email account passwords, and even SSL certificates.”
On Mastodon, security researcher Marc Rogers posted instructions from Sisense on which types of access credentials should be reset (see below).
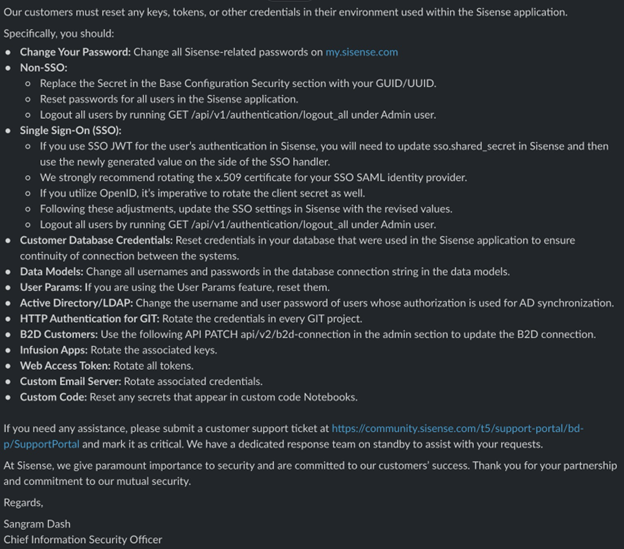
Sisense customer credential reset instructions.
In the same thread, Rogers said, “[M]embers of the cybersecurity community and agencies all over the world have worked this intensely over the last few days.” He thanked agencies from the United States, the United Kingdom, New Zealand, and Canada for “amazing collaboration” in containing the Sisense breach.
We don’t have the precise details about what went wrong here, but if independent reporting is to be believed, it looks like Sisense has some questions to answer, at the very least.
But, as per last week, we are left wondering why government agencies are spending time and effort cleaning up problems created by the private sector. One answer, of course, is that they have to and we would be much worse off if they didn’t.
But the broader systemic question is why can private-sector companies underinvest in security and get everyone else to bear the cost?
Dependency on Microsoft a Strategic Risk
Wired has a good examination of the U.S. government’s dependence on Microsoft and how the company is “insulated” from accountability, despite a series of entirely avoidable security failures.
The author, Eric Geller, says this stems from a combination of factors, including that Microsoft is the government’s most important technology supplier; the company is a critical partner for government cybersecurity initiatives; and it has undertaken politically savvy lobbying and marketing efforts over decades.
The overall message of the piece is that Microsoft is still not treating its security problems with the seriousness they deserve, and it examines what should be done to force Microsoft to lift its game when it comes to security.
Geller’s piece links to news that CISA is modernizing its information technology environment and creating a new “greenfield” architecture. This effort is to develop a more secure environment that can be an example implementation for other agencies.
This architecture doesn’t rely on Microsoft’s Active Directory, which is at least a start in giving government agencies options and increasing pressure on the company to improve its security. More of this, please.
When coupled with the U.S. government’s dependence on its services, Microsoft’s lackluster focus on security is a long-term national security problem. Cutting that dependency will take time, but it has to be done.
U.S. Cyber Command Hunts Authoritarian States
In testimony to the Senate Armed Services Committee, the new head of U.S. Cyber Command and the National Security Agency, Gen. Timothy Haugh, provided a written overview of the state of the world from Cyber Command’s perspective.
This included brief summaries of major cyber threat actors.
Haugh described the People’s Republic of China (PRC) as “our pacing challenge” and said it employs “the world’s largest cyberspace operations workforce.” Cyber Command’s main focus is “defending against the PRC’s persistent access and pre-positioning for attack on U.S. critical infrastructure systems.”
Russia is also “an acute threat,” although its focus on the conflict in Ukraine has diverted its attention from other worldwide intelligence efforts. Interestingly, Cyber Command assesses that “Moscow likely views the upcoming U.S. election as an opportunity for malign influence” and that it will “most likely” interfere with elections in the United States and Europe this year.
Iran is particularly focused on disrupting critical infrastructure, and Cyber Command has “supported significant efforts to bolster the cyber defenses of Israel and other regional partners” since the start of the Israel-Hamas war.
North Korean cyber forces are “increasingly capable,” although Haugh’s testimony seems to treat North Korea like a tertiary concern compared to the other threat actors mentioned.
When it comes to non-state actors, Haugh says the National Security Agency and Cyber Command have an enabling role “to disrupt ransomware, cryptocurrency theft, and other criminal activities.”
In 2023, Cyber Command carried out 22 “hunt forward” operations in 17 countries. These are efforts to find and disrupt adversary activity on partner networks.
Haugh says these missions led to public releases of more than 90 malware samples. These disclosures “frustrate the military and intelligence operations of authoritarian regimes,” according to Haugh’s testimony. You can almost hear the happiness in these words.
Three Reasons to Be Cheerful This Week:
- Identifying the real LockBit criminals: Law enforcement authorities have said they’ve been able to identify the real-world identities of “a good number” of LockBit ransomware affiliates. The LockBit ransomware group takedown operation obtained a list of about 200 potential affiliates. It won’t be easy to arrest affiliates even once they are identified, but it is a start.
- CISA is opening its malware analysis service: CISA has announced that its malware analysis service, Malware Next-Gen, will be opened to the private sector. The service had previously been open only to government customers.
- 77 arrested in Zambia for internet fraud: Zambian law enforcement agencies arrested 77 people, including 22 Chinese nationals who were allegedly engaged in internet fraud scams. The raid of Golden Top Support Services found 11 SIM boxes and 13,000 SIM cards.
Shorts
When Crypto Crime Doesn’t Pay
An ex-Amazon engineer, Shakeeb Ahmed, was sentenced to three years in prison for hacking two separate cryptocurrency exchanges. After both of these hacks he attempted to negotiate with the victim exchanges to get his actions recognized as “bug bounties” rather than outright thefts, in exchange for returning some of the money.
Separately, another indictment unsealed this week alleges that Charles O. Parks III, also known as CP3O, stole $3.5 million worth of cloud computing services to mint $1 million of cryptocurrency.
Skilled Hackers Prefer the Sunshine
TechCrunch has an interesting interview with Yevhenii Panchenko, the chief of Ukraine’s National Police cyber department. Panchenko describes how Russia recruits new hackers by initially giving them small jobs and ratcheting up the tasks if they are successful.
Despite the difficulties in prosecuting hackers in the midst of a war, Panchenko takes the long view. He says that although a regular soldier “will probably never come to the European Union and other countries,” skilled hackers will “prefer to move to warmer places and not work in Russia because [they] could be recruited to the army.” So collecting evidence and sharing it with partners is important.
AI Election Interference Tracker
The Rest of World publication has launched an AI election interference tracker. It’s already assembled an interesting collection of examples.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq look at Google’s review of zero days in 2023. They discuss what this kind of information tells us and how Google’s perspective influences the report.
From Risky Biz News:
PuTTY crypto bug exposes private keys, may lead to supply chain attacks: A team of German academics has discovered a crypto vulnerability in PuTTY, an extremely popular SSH and Telnet client for Windows users. The vulnerability allows attackers who run malicious SSH servers to observe cryptographic signatures and recover a user’s private key. This allows attackers to connect to systems where the private keys are being used for authentication.
But the vulnerability’s main impact is on source code repositories if they’ve been managed via a client that embeds PuTTY. Attackers can look at a project’s past signed public commits and then determine a developer’s private key. As the U.S. National Vulnerability Database points out in its description of the vulnerability, this opens the door to supply chain attacks where threat actors can submit “signed” malicious code to legitimate projects.
[more on Risky Business News]
Palo Alto Networks scrambles to push zero-day patch
[Editor’s note: Palo Alto has since put out patches for the latest releases of PAN-OS and announced a rollout schedule for the rest.]
Palo Alto Networks scrambled over the weekend to release a software patch for its firewall devices. The patch is intended to fix a zero day (CVE-2024-3400) in the GlobalProtect VPN feature of PAN-OS, the firmware that runs on Palo Alto’s firewalls.
Security firm Volexity discovered the attacks, which the company attributed to a group it tracks as UTA0218. Palo Alto tracks this as Operation MidnightEclipse. Volexity described the group as a state-backed threat actor but did not link the group to any country.
Volexity assesses that it is highly likely UTA0218 is a state-backed threat actor based on the resources required to develop and exploit a vulnerability of this nature, the type of victims targeted by this actor, and the capabilities displayed to install the Python backdoor and further access victim networks.
According to a timeline published by Volexity, the attacker appears to have developed and tested the zero day at the end of March.
[more on Risky Business News]
Pegasus in Poland: Poland’s prosecutor general says the country’s former ruling government has hacked 578 individuals with the Pegasus spyware. The hacks were carried out by three Polish services between 2017 and 2022. The findings are part of an investigation into abuses performed by the former government, controlled by the Law and Justice Party. Previous reports have accused former Polish officials of using the spyware against opposition members, prosecutors, and journalists. [Additional coverage in Wiadomosci]





