Beyond Economic Espionage
Foreign intelligence services aren’t simply stealing valuable assets to help their businesses—they’re engaging in an assortment of activities to ensure their countries dominate economically.
Published by The Lawfare Institute
in Cooperation With

Much of the reporting on nation-state threat activity is focused on the latest cyber intrusion, such as the SolarWinds intrusion or the intrusion of numerous coronavirus vaccine developers. These intrusions are often breathlessly portrayed as brazen and sophisticated attacks on well-defended companies—or government agencies, as the case may be. The stories, unfortunately, underrepresent the full scope of what is transpiring.
Inter-state competition is bleeding into every aspect of the economy, and the gravity of the threat U.S. businesses face from nation-states and their proxies cannot be overstated. As we have written, today’s most important geopolitical battlespace is the private sector. While there are countless economic sectors within which competition is taking place, it is most savage in those on which modern developed economies most depend—such as advanced technology, cyberspace, health care, insurance and finance, to name just a few. Attackers target groundbreaking technology, but also essential personnel, innovative business practices, unique data sets, and plans and strategies. Mastery of these building blocks allows nation-state competitors to grow successful companies in a wide variety of areas.
In this competition for economic advancement and industry domination, foreign intelligence services are using an assortment of illicit tactics beyond economic espionage to advance nation-state objectives. These services aren’t simply stealing valuable assets to help their businesses—they’re engaging in diverse activities to ensure they dominate economically. While the list continues to grow, such tactics include stock market, social media, and regulatory manipulation; data harvesting; national champion building; digital bank robbery; and even the destruction of corporate assets.
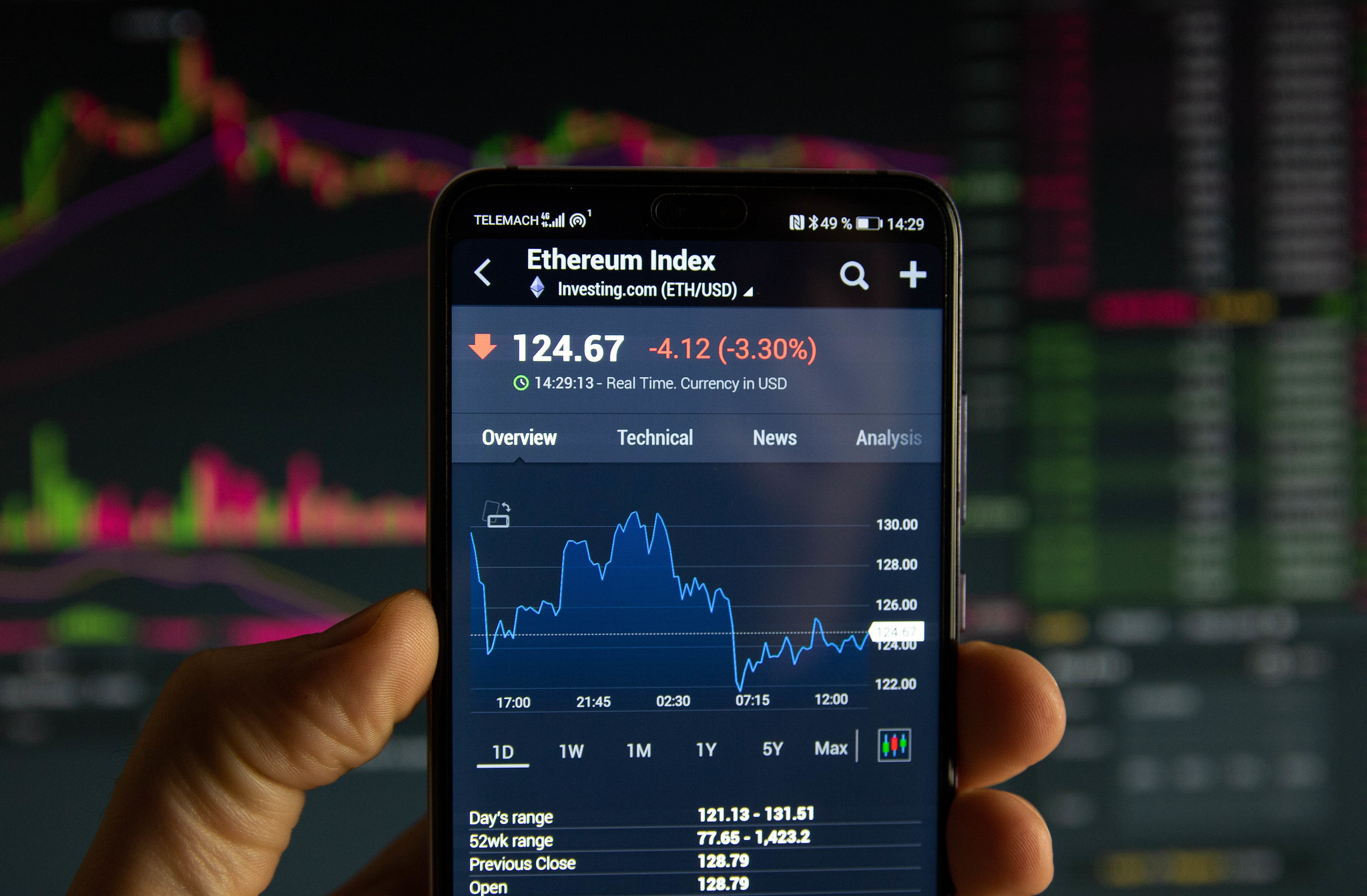
Stock Market Manipulation
In 2015, prosecutors filed a complaint against three Russians in New York City. Among other things, the complaint alleged that the three were working for the SVR, Russia’s external intelligence agency, and were attempting to gather intelligence about high-speed trading, automated trading algorithms and the destabilization of markets. There was much speculation at the time as to what exactly Russia’s objective was. Why would the SVR want this information? Perhaps the agency was trying to help improve the operation of Russia’s stock markets and protect them from outside manipulation. Or perhaps it was preparing to attack U.S. stock markets.
This was not the first time that Russia had attempted to covertly obtain information about how U.S. stock markets work. In 2010, Russian hackers penetrated the NASDAQ stock exchange. It appears these hackers may have opened the door that then allowed a Chinese intrusion, as well as access by several other groups, including criminal hackers. Although there were indications that a particularly large cache of data was exfiltrated, the investigation revealed little detail on what information was taken. Unfortunately, daily records of server activity were nonexistent, making it extremely difficult to piece together what had transpired.
So while the exact target of the intrusion was not clear, external events and the evidence of some type of data exfiltration suggest that the Russian hackers sought to better understand how NASDAQ worked. Russia at the time was attempting to strengthen its own stock exchanges and make them world class, and information about how NASDAQ runs its exchange would have been extremely helpful. However, the malware used for the intrusion wasn’t designed only to steal data. It also had the capability to “create widespread disruption” in the network. and potentially the stock exchange itself. This capability suggested that Russia may also have been looking to lay the groundwork for a future disruption.
It’s unclear whether Russian intelligence has continued to try and penetrate stock exchanges in recent years. If Russia really has been looking for ways to destabilize or disrupt stock market operations, it may have turned to another approach.
The recent cyber intrusion into SolarWinds, reportedly at the hands of Russian intelligence, may illustrate just such an alternate methodology. There’s no need to directly target an individual stock exchange when you can ride on the coattails of a company’s software update (in this case, that of SolarWinds) and penetrate thousands of businesses—especially those with access to other companies’ information technology infrastructure and their data, like Microsoft (via the company’s Azure Cloud infrastructure) or the cybersecurity firm FireEye. The working assumption of experts is that the intruders must have exfiltrated data, though the amount of data exfiltrated is unknown.
Considering Russia’s history of intrusions, it’s worth considering whether this access to such a wide swath of companies could have positioned Russia to cause enormous market havoc if it so wished. Time and again, Russia has demonstrated the ability to cause such damage. Businesses should be asking under what conditions the Russians would execute an attack and whether they would be positioned to withstand it.
Social Media Manipulation
The recent Reddit-GameStop kerfuffle offers an example of the ease with which lightly organized groups of individuals can affect the market. Keith Gill, who also goes by the moniker Roaring Kitten, began posting on Reddit in summer 2019 about his investment in the video game retailer GameStop. Gill made TikTok and YouTube videos and continued to push the stock over social media, driving the share price higher and higher as his following increased. The goal was in part to hurt the large hedge funds that had been betting against GameStop, some of which purportedly experienced huge losses. On Jan. 26, Gill boasted that his initial $53,000 investment had increased in value to $48 million. GameStop’s share price remained volatile through the end of January.
To date, there is nothing to indicate that any of the activity was influenced, much less directed, by an outside power. But the various intelligence services were surely watching and learning. Any intelligence service wanting to put this methodology into action would need to be adept at manipulating social media forums. Unfortunately, many have been honing that skillset in recent years.
Russia’s efforts to manipulate social media have been well documented in both government and private reports. Russia has employed such tools to sway elections as well as to simply sow chaos and discord in order to to discredit governments. Actors linked to the Russian government have used thousands of fake accounts to create or influence the narrative on a number of important issues.
This approach to social media proliferates in the private sphere, as well. Individuals often take to the internet to air their grievances, warranted or not, and discredit others. Recent reporting from the New York Times describes numerous sites on which people can post sordid accusations about others without having to provide validation. Some of the websites to which the material is posted charge those accused an exorbitant fee to remove the information. It doesn’t take a stretch of the imagination to understand how intelligence services or other organizations could use similar tactics to smear others, like a competitor business or its executives.
Not wanting to be left behind, China appears to have adopted Russian social media manipulation tactics to achieve better market conditions for Chinese companies. A recent social media campaign criticized a Belgian regulatory policy that would limit Huawei, a company with connections to the Chinese government, from obtaining 5G contracts. Fourteen Twitter accounts, using “computer generated profile pictures” and purported to be associated with individuals with telecommunications experience, laid the groundwork for the campaign. Once the initial “talking points” were tweeted from the 14 accounts, official Huawei Twitter accounts picked up the information and blasted it to their millions of followers. Huawei says it has started an internal investigation to get to the bottom of this.
The case illustrates the use of social media to try to manipulate the regulatory environment. The goal was not to sow discord as it so often seems to be with Russian campaigns, and it was not to discredit another person or organization—which is becoming more common in civil society. The goal was to influence a regulatory matter of great importance to a pivotal Chinese company. This technique of “curating the environment” is a tried-and-true tactic of Chinese intelligence. Rather than trying to directly influence a particular individual or decision, as Russia does, China often covertly tries to change the conditions of the environment so that, ultimately, decisions are made in the country’s favor.
Regulatory Manipulation
In addition to weaponizing social media to affect regulatory matters, China sometimes also uses individuals to more directly influence particular regulation. Recent reporting describes how suspected Chinese spy Christine Fang targeted multiple U.S. politicians at all three levels of government. According to Axios, Fang, who operated in the United States from 2011 to 2015, first came to the attention of U.S. counterintelligence officials due to her contacts with a suspected Ministry of State Security intelligence officer operating out of the Chinese Consulate in San Francisco. The report concludes that Fang and the intelligence officer appeared to have similar modus operandi—developing political intelligence and conducting influence operations in the Bay Area. Fang’s handlers, according to U.S. officials, were back in China. Her activities were reported to be far ranging, simultaneously cultivating relationships with local- and state-level officials and developing contacts with individuals trying to break into the federal ranks. She purportedly used “campaign fundraising, extensive networking, personal charisma, and romantic or sexual relationships … to gain proximity to political power.”
As the Fang case shows, local and state governments in the United States and elsewhere often represent a soft underbelly that is highly susceptible to foreign government influence. U.S. officials at this level are rarely savvy to influence operations or elicitation techniques used by intelligence operatives. Foreign intelligence services know this and dedicate resources accordingly. Not only is it usually easier for foreign intelligence operatives to form relationships with local and state politicians than with those at the federal level, but the operations also can bear tremendous fruit. A significant amount of economic decision-making occurs at the local and state levels. For example, politicians, who are regularly seeking investment in their jurisdictions, can offer a variety of economic incentives—such as tax breaks— to businesses, even foreign ones. According to Axios, China was likely aiming for just such influence over local-level investment issues in cases like Fang.
Data Harvesting
Some Americans have gotten used to providing their data to businesses, but foreign intelligence agencies are looking for that data too. Consider TikTok, a Chinese-owned video-sharing social networking site. While the extent of the data that TikTok collects from its users continues to be debated, there appears to be a growing consensus that the company engages in far-reaching data harvesting. It remains in dispute, though, whether the People’s Republic of China (PRC) intelligence services have access to what TikTok collects.
Much of the reporting and debate around TikTok focuses on the so-called lack of a “smoking gun”: Where is the direct evidence that the intelligence services have access to the data? But this focus is flawed for two reasons. First, the idea of a “smoking gun” is about circumstantial or indirect evidence (there’s smoke coming out of the gun, so it was probably just fired) and not about direct evidence (there’s a video of an individual firing the gun). By this standard, a lot of circumstantial evidence indicates the PRC intelligence services have access to TikTok data. Its parent company, ByteDance, has explicitly said it will deepen cooperation with the Chinese Communist Party; the PRC has a national security law that requires companies in China to cooperate with demands from intelligence and security officials; and TikTok uses a significant amount of PRC infrastructure to support its operations.
Second, it would be difficult to collect direct evidence that PRC intelligence services were accessing TikTok data. Unless the services were being extremely sloppy, the data would be harvested discreetly in China—a practice made possible by TikTok’s widespread use of PRC infrastructure. The lack of direct evidence in this example reveals little about the sanctity of TikTok data. U.S. businesses and citizens need to use available information to carefully weigh the risks and benefits of using apps like TikTok, Kuaishou (a similar video-sharing app) or even WeChat.
National Champion Building
The PRC intends to build world-dominating companies across a wide range of industries. These so-called “national champions” are often private businesses that receive government assistance in the form of unfair support in market competition and eased regulatory conditions, both of which lead to domestic success and promote greater resilience in international markets. While there are few, if any, areas of business the PRC doesn’t intend to dominate, certain industries have been prioritized for development. If an American business is in such an industry, it is in the crosshairs—and must prepare accordingly. Businesses with technology, know-how or some other special expertise that the PRC needs for development could be identified as particularly lucrative targets.
Many such businesses will be welcomed into China’s huge and growing market, and the prospect of tens or hundreds of millions of potential customers is often too tantalizing for companies to resist. But the companies need to understand that they could be trading long-term prosperity for short-term profits. The PRC seems to consider almost every successful foreign company in China as a market failure on its part. In other words, certain foreign companies are successful in China only because the PRC has failed to meet the market’s needs with a Chinese company. This explains why the PRC intends to eventually replace almost every successful foreign company in China with a Chinese one. Time and again, once the PRC has extracted whatever technology, know-how, or data it deems of value from heretofore successful foreign companies operating in China, they experience regulatory reviews, tax problems or myriad other supposed issues that make doing business in China not only unprofitable but almost impossible.
Recent reports may indicate that Tesla is nearing the end of its successful run in the PRC. BYD, a Chinese company, recently surpassed Tesla to become the top-selling electric car brand in China. And almost like clockwork, Tesla has gone from darling of the Chinese Communist Party—Tesla CEO Elon Musk was offered the Chinese equivalent of a green card by Chinese Premier Li Keqiang—to being questioned by five different regulatory agencies in China about quality control issues. More troubling for Tesla, state-backed news agencies Xinhua and Global Times have piled on with negative commentary, likely in an attempt to begin swaying public opinion against the company.
It’s possible that this is just the opening salvo in a bid to renegotiate the unique deal Tesla received in China, as Tesla retained full control of its Chinese Gigafactory. Or it could be that the PRC has already finished extracting whatever it needed—and now it’s time for Tesla to go.
Bank Robbery and Destruction of Corporate Assets
North Korean activities are also worth attention. The regime in Pyongyang has often acted more like an organized crime syndicate than a typical nation-state, engaging in everything from highly sophisticated bank robbery to wide-scale destruction of corporate assets in the Sony hack. While the bank robbery resulted in an $81 million loss, the country would have succeeded in stealing $1 billion if not for a diligent worker at the Federal Reserve Bank of New York who noticed a typo in the fraudulent transaction request. Sony was said to have experienced a loss in the tens of millions of dollars, but that is likely a vast underestimate, as much of the damage couldn’t be adequately quantified. The company suffered a massive destruction of corporate assets and exposure of employee personal information.
What’s more, North Korea has started to sell its services to third parties. In other words, highly skilled North Korean hackers can be hired by other nation-states, companies, criminal groups, or individuals to get at a company’s money, data and other important assets.
***
Foreign intelligence services are focused on U.S. businesses like never before. The threat they pose is multifaceted. It encompasses far more than economic espionage—and robust cyber defense, while critical, provides insufficient defense. Businesses, if they want to survive and thrive, must develop a better understanding of the various competitive—or, rather, anti-competitive—tactics used by intelligence agencies against them.





