China vs. World: Cybersecurity Reporting Duel
The latest edition of the Seriously Risky Business cybersecurity newsletter, now on Lawfare.

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz.
China vs. World: Cybersecurity Reporting Duel
Western cybersecurity agencies are co-authoring reports with an increasing number of overseas agencies into Chinese cyber activity. And China doesn’t seem to like it.
The Australian Signals Directorate (ASD) last week issued an advisory co-authored with German, Korean, and Japanese intelligence; cybersecurity and law enforcement agencies; as well as the standard Five Eyes agencies that regularly contribute to advisories. The advisory documented two successful compromises of Australian organizations and resulting investigations by the Australian Cyber Security Centre (ACSC). The agencies attributed the compromises to APT40, a People’s Republic of China (PRC)-sponsored group that operates on behalf of the Ministry of State Security (MSS). The report documents what it calls a “notable” shift in tradecraft, away from using hacked websites for command and control to using compromised small office/home office devices to relay communications.
There is only a tiny amount of information in the report that could be ascribed to organizations other than ASD. The corralling of international agencies as authors is all about presenting a united front against Chinese cyber operations.
China, however, is pushing back by issuing its own reports on purported U.S. activity or attempting to cast doubt on reports into its own behavior.
Last week, for example, China’s National Computer Virus Emergency Response Center (CVERC) attempted to cast doubt on reports about Volt Typhoon, a PRC-sponsored group suspected of compromising U.S. critical infrastructure for potential disruption in the event of a military conflict. The CVERC report claims U.S. intelligence agencies fabricated Volt Typhoon to gain increased budget from Congress.
In September 2023, the MSS accused the National Security Agency (NSA) of hacking Huawei, and in 2022 Risky Business News covered “hilariously bad” reports claiming NSA hacking of a Chinese university. (To be clear, we don’t doubt that the NSA is hacking PRC targets, but Chinese reports about this activity are woefully lacking in concrete information.)
So, more robust reporting about Chinese cybersecurity operations may be causing an impact, at least in fueling counter-reports. Regardless, establishing a united front with international partners about PRC-based threat actors is still a worthwhile endeavor.
U.S. Outs Russian Government Social Media Manipulation
The U.S. Department of Justice has spelled out the direct links between the Russian government and a social media bot farm spreading disinformation across the U.S. and Europe. The botnet operated on X (formerly Twitter) and promoted narratives favorable to the Russian government. The Justice Department spelled out links to the Kremlin in a press release and associated affidavits released with the announcement of an operation to take down the botnet.
The released documents spell out how the Kremlin, the FSB (Russia’s Federal Security Service), and a deputy editor-in-chief of the state-run Russian media outlet RT (formerly Russia Today) were involved in the creation, direction, and operation of the social media influence operation.
This Russian influence operation is not surprising, but it is interesting to see the U.S. government devoting so much effort to the issue. The affidavit says an unspecified “US agency” tipped off the FBI to the presence of the botnet.
And it is not just the U.S. government. Along with the FBI and Cyber Command, Canadian and Dutch intelligence and cybersecurity agencies released a joint cybersecurity advisory describing the technology behind the social media bot farm, including how it used a custom artificial intelligence system. How the botnet operates is described here on Risky Business News.
Gaping Security Holes in the U.S. Federal Government
Last week, the Cybersecurity and Infrastructure Security Agency (CISA) published an excellent report covering an eight-month-long red team operation against a large unnamed U.S. civilian federal government agency. The report is a detailed real-world case study of how common network misconfigurations can be exploited to own an agency network and even pivot into an external organization.
CISA calls this a “SILENTSHIELD” red team assessment comprising a “no-notice, long-term simulation of nation-state cyber operations”:
The team mimics the techniques, tradecraft, and behaviors of sophisticated threat actors and measures the potential dwell time actors have on a network, providing a realistic assessment of the organization’s security posture.
In other words, these are “gloves-off” security assessments that don’t have the limited scope and short time frames that often neuter red team engagements.
The engagement comprised an “adversary emulation phase,” in which CISA gained unrestricted privileged access to the unnamed agency’s network, and a three-month “collaboration phase,” in which it helped improve the organization’s cybersecurity capabilities.
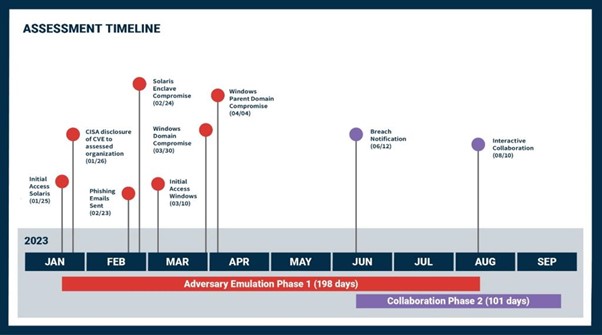
Figure 1: SILENTSHIELD Assessment Timeline
CISA gained initial access by taking advantage of an unpatched remote code execution vulnerability in a web server. The report notes that CISA informed the target agency of the unpatched device, but the agency took over two weeks to rectify and did not thoroughly investigate the affected servers. This was a missed opportunity according to CISA, as the impacted agency would have discovered indicators of compromise (IOCs) that should have led to full incident response.
CISA leveraged initial access into full compromise of the agency’s Solaris enclave. This included access to sensitive systems including web applications and databases. To access the agency’s Windows environment, CISA created a target list of employees whose jobs involved public interaction with open-source research and successfully phished one of them.
Once on the Windows network, CISA “found a password file left from a previous employee on an open, administrative IT share, which contained plaintext usernames and passwords for several privileged service accounts.” One of these accounts had domain administrator privileges for the parent domain and another had administrative permissions for most servers in the domain. Passwords for these accounts had not been updated in over eight years.
While in the target organization, CISA was able to take advantage of relationships with trusted partners to pivot into another civilian federal government agency. The report notes:
These cross-organizational attack paths are rarely identified or tested in regular assessments or audits due to network ownership, legal agreements, and/or vendor opacity. However, they remain a valuable access vector for advanced persistent threat (APT) actors.
The “lessons learned” section of the report is excellent because it covers the gamut from technical to organizational shortcomings. At the technical level, it points out that the agency had “insufficient controls to detect malicious activity” and “ineffective logging, collection and analysis.”
CISA says the agency’s “hyper-focus” on detecting malicious activity using “known-bad” IOCs hampered defenders’ efforts against threat actors using new and different tactics, techniques, and procedures (TTPs). The report says the target agency was “accustomed to catching internal red teams that used specific TTPs; introducing a new ‘threat actor’ with new TTPs sidestepped nearly all detections.”
The report notes that decentralized teams with bureaucratic communication hindered defense. There were too many teams working in an uncoordinated way, meaning it was very difficult to build a comprehensive picture of possible threat activity.
In our view, this report is a companion piece to an advisory CISA and NSA released last year that warned about common cybersecurity misconfigurations the agencies’ red and blue teams find in large organizations. That advisory warned that misconfigurations are common, going so far as to describe “a trend of systemic weakness in many large organizations, including those with mature cyber postures.” This report illustrates how these misconfigurations can be exploited in a real network. That makes it relevant to many organizations.
CSE Sheds Some Light on Ransomware Disruption
The Communications Security Establishment Canada (CSE), the country’s equivalent of the NSA, has revealed it last year disrupted an ongoing foreign ransomware attack on Canadian critical infrastructure. The operation was revealed in CSE’s latest annual report, released late last month. The report says:
While the Cyber Centre [Canada’s equivalent of the U.K. NCSC or U.S. CISA] worked to mitigate the compromise within Canada, CSE’s foreign cyber operations team took action in cyberspace. The [defensive cyber operation] interfered with the cybercriminals’ foreign servers, reducing the effectiveness and profitability of their activities. Most importantly, CSE’s actions reduced the impact of the incident on the victims.
CSE categorizes this as a defensive cyber operation, used to protect systems during major cyber incidents “when cyber security measures alone are not enough.”
CSE also proactively disrupts foreign-based threats in what it calls active cyber operations (ACOs). The annual reports says:
CSE also continued its ongoing ACO campaign to disrupt the activities of foreign ransomware groups. Working with Five Eyes partners, CSE used ACO to undermine the activities of foreign ransomware groups and to degrade the online tools they use. These ongoing operations make it harder for cybercriminals to launch ransomware attacks against Canadian organisations and to profit from the theft of Canadian data. CSE prioritises its operations based on the Cyber Centre’s assessments of which ransomware groups pose the greatest threat to Canada.
Cyber operations agencies can be notoriously secretive, so it is nice to get a little vignette about events in the counter-ransomware space.
Three Reasons to Be Cheerful This Week:
- Passkeys make Google’s Advanced Protection Program (APP) easier: The APP, Google’s highest level of account protection, has traditionally required two hardware security keys (in case one is lost or broken). Getting these keys has been difficult for some users, such as “a journalist covering a war zone, a traveling campaign worker, or a business leader taking a last-minute trip,” Google says. But now people can mix and match passkeys with hardware security keys (enrolling with two passkeys, for example, or using one passkey and one physical device).
- Better, faster Windows updates: Microsoft has announced that Windows 11 will get “checkpoint cumulative updates” that will involve “smaller, faster and more sustainable updates.” This will push out feature and security updates via smaller incremental updates that contain only the changes from the previous checkpoint.
- Chinese telecommunication companies kicked from German networks: Critical components from Huawei and ZTE will be barred from German 5G core networks by the end of 2026, Interior Minister Nancy Faeser announced last week.
Shorts
CDK Breach Not Material, Except for Customers
CyberScoop examines how new U.S. Securities and Exchange Commission (SEC) disclosure rules have been interpreted in the recent ransomware attack on automotive software-as-a-service company CDK Global. While several of CDK Global’s customers issued SEC filings indicating the incident had caused short-term impacts and might be material in the longer term, CDK Global’s parent firm, Brookfield Business Partners, has not filed with the SEC.
In a press release, parent firm Brookfield said, “We do not expect this incident to have a material impact.” It appears that CDK Global may have paid a $25 million ransom, but this still seems fair enough given that Brookfield booked $96 billion in revenue in 2023.
The SEC has actually issued guidance about what to do here, and it essentially boils down to “just use the right form.” If you’ve determined that an incident is material, disclose it under Item 1.05 of Form 8-K, “Material Cybersecurity Incidents.” If the incident is immaterial, or if you haven’t yet determined whether it is material, use Item 8.01 of Form 8-K, “Other events.”
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq discuss Shashank Joshi’s notes from a recent Oxford Cyber forum. Topics include the role of zero-days and who is ahead when it comes to offensive cyber operations.
From Risky Biz News:
Ransomware attacks increase hospital mortality rates: A white paper published last year by academics from the University of Minnesota’s medical school has looked at the aftermath of ransomware attacks on U.S. hospitals and found evidence to suggest that mortality rates typically increase by around 20 percent.
The study looked at hospital admissions before, during, and after a ransomware attack, at the hospital’s profits, and at reported patient deaths.
Researchers said the most affected category were patients who were already hospitalized at the time of the ransomware attack, compared to patients who were admitted after, where hospital staff could adjust procedures to take into account unavailable information technology (IT) systems.
[more on Risky Business News]
Squarespace DNS hijack spree hits crypto sites; everyone else watch out! At least four cryptocurrency platforms hosting their domains on Squarespace have been hit by DNS hijacks over the past week.The Celer Network, Compound Finance, Pendle Finance, and Unstoppable Domains reported losing control over their official websites on Thursday and Friday last week.
The hijackers pointed the domains to malicious servers hosting wallet-draining phishing kits.
According to a report published by a team of security researchers from Paradigm and Metamask, the affected domains were previously hosted on Google’s now-defunct domain business. Squarespace acquired Google Domains earlier in June 2023 and moved all Google customers to its infrastructure in June this year. The research team says domains migrated from Google Domains to Squarespace had their multi-factor authentication disabled as a technical measure to prevent admins from being locked out of their accounts after the migration.
[more on Risky Business News]
Apple warns iPhone users of new spyware attacks: Apple has sent this week a new batch of notifications about possible infections with mercenary spyware to iPhone users across 98 countries. This was the company’s second wave of notifications it sent this year after a first round back in April.
[more on Risky Business News]
A ransomware attack is putting lives at risk across South Africa: For the past two weeks, a ransomware attack has been wreaking havoc among health care services and putting lives at risk across South Africa. The incident took place on June 22 and hit the National Health Laboratory Service (NHLS), a South African government organization that does lab work for the country’s hospitals.
The attack and subsequent IT outage crippled 265 NHLS laboratories and their ability to process blood work. According to a report from the Cape Independent, the labs are behind on over 6.3 million blood tests. The lack of proper blood work is delaying accurate diagnostics and has postponed operations, putting countless patient lives at risk.
A hematologist from Johannesburg described the situation as “dire,” with patients in emergency wards and intensive care units around the country being in “fatal danger.”
[more on Risky Business News]





