Data Brokers, Military Personnel, and National Security Risks
A new study dives into the multibillion-dollar data brokerage ecosystem and the kinds of data that U.S. companies gather and sell about service members, veterans, and their families.

Published by The Lawfare Institute
in Cooperation With

“For sale: data on US servicemembers—and lots of it,” reads a recent Politico headline. The article describes a new report we authored for the data brokerage research project at Duke University’s Sanford School of Public Policy, focused on data brokers, the sale of data about U.S. military personnel, and its risks to national security. It’s the product of a 12-month study, sponsored by the U.S. Military Academy, diving into the multibillion-dollar data brokerage ecosystem and the kinds of data that U.S. companies gather and sell about active-duty military service members, veterans, and their families.
In the course of our study, we were able to purchase from data brokers sensitive data about active-duty members of the military, veterans, and their families. This includes nonpublic, individually identified, and sensitive data, such as health data, financial data, and information about religious practices. We bought this and other data from U.S. data brokers via a .org and a .asia domain for as low as $0.12 per record. Overall, the data brokers we contacted had inconsistent methods for determining the identity of customers and what they might use the data for—suggesting a concerning lack of industry best-practices within a highly unregulated data brokerage ecosystem. For instance, one data broker told us that if we paid by wire instead of credit card for a data set on military personnel, we could skip a customer verification process (which we did).
Amid policy attention to foreign intelligence operations targeting the U.S., the lack of a comprehensive federal consumer privacy law, and the risks of different foreign apps and tech products, foreign and malicious actors could access brokered data to target active-duty military personnel, veterans, and their families and acquaintances for profiling, blackmail, information campaigns, and more.
Some mitigating measures are available to the Department of Defense and regulatory agencies such as the Federal Trade Commission (FTC) and the Consumer Financial Protection Bureau (CFPB). But at the end of the day, this is a problem for Congress to address. A comprehensive privacy law, combined with additional, focused national security controls from Congress and the executive branch, would best help to tackle these risks at the intersection of data privacy, U.S. military personnel, and national security.
Data Brokers Selling Military Service Members’ Data
In a report from our team in August 2021, we identified multiple data brokers advertising the fact that they had data related to U.S. military service members and veterans. This information led to two questions: What kinds of data are data brokers currently gathering and selling related to U.S. military service members and veterans? And what is the risk that a foreign adversary could exploit the data brokerage ecosystem to access this data on U.S. military service members and use it in harmful ways? Data brokers are collecting and selling a wide range of data about U.S. military personnel—including related to health conditions, finances, health, politics, religion, children, geolocation, and more—and foreign adversaries could exploit it to profile, blackmail, and target military personnel and their families.
To assess the market, we first created a list of data broker websites, drawing from the Vermont and California state data broker registries. (Under their applicable laws, Vermont and California require companies defined as “data brokers” to provide the respective state governments with information such as their company name, updated company website URL, and company contact information, which is then published to a public registry.) Combining both data sets gave us a list of 561 websites that fell within the collective Vermont and California definitions of a “data broker.” Removing broken URLs and other bad data yielded 533 websites. We then built and ran an automated scraping program on those 533 websites, looking for terms such as “DoD,” “military,” “veteran,” and “department of defense.” The list of terms also included “pregnant,” “alzheimers” [sic], and “elder,” among others, because they relate to other workstreams in our data brokerage research.
In total, “military” had 7,278 hits and “veteran” had 6,776 hits across the collective 533 data broker websites. Examining the context for each hit—that is, the sentence or line of code surrounding each mention of “military” or “veteran”—made clear that the hits related to everything from marketing blogs to the names of specific data sets for sale. For example, many brokers advertise data sets pertaining to U.S. military service members’ hobbies, careers, and interests. These include data sets with such titles as “Veterans that own a motorcycle,” “military readers,” and “Veteran Owned Construction Companies.” One broker advertises data on veterans who are “responsive … to one or a variety of causes” (the causes were not specified), claiming that “[g]iving back and helping others is something that is in their heart & soul …. You can already see them opening up their wallet for your offer today.” That same broker advertises other demographic information related to those individuals, including “their branch of service, income, age & even gender.” One so-called “people search website”—a type of data broker that scrapes public records and makes them available for search and sale online—describes its ability to find a deceased “Veteran’s claim or discharge number” by searching death records. The thousands of hits across hundreds of websites demonstrate that these data categories can quickly and easily be found online.
With these findings in mind, we set out to then purchase data from U.S. data brokers about U.S. military personnel—through both a .org domain (the “U.S. side”) and a .asia domain (the “.asia side”). For the U.S. side, we set up a U.S. domain, datamarketresearch.org, and set up an intentionally vague, associated email address. We used wiped laptops, Google Voice numbers, and other measures to minimize the risk that data brokers gathered additional data about our research team during the research process other than the information we provided. Our team then contacted 12 U.S. data brokers asking to buy data about U.S. military personnel. These brokers are not identified by name in our report and are instead described as Broker 1, Broker 2, and so forth.
The data brokers’ controls—and willingness to sell—were inconsistent; two brokers refused to sell to us based on our lack of a website and the fact that we were not a “verified” company. One location data broker said it would not sell geolocation data around “sensitive” locations, including military sites, but could provide geolocation data on many other areas of the country. But several brokers were willing to sell that information, and multiple data brokers sent us lists of hundreds of identifiable demographic variables that we could select from within their consumer databases. This is a relatively standard practice for data brokers but underscores that a prospective buyer could purchase many different data points on individuals, selected from a large menu of options. Two brokers requested that we sign nondisclosure agreements (NDAs) covering our interactions with the broker, details on the data available for purchase, and any purchased data sets. We did not sign any NDAs and did not purchase from these brokers.
Our team ultimately purchased five data sets from three of these brokers through our U.S. .org domain and email. The data sets were all individually identified by name and are described in the figure below. They included name, home address, email, specific branch and/or agency, health conditions (such as “heart problems,” “asthma,” and “bladder control difficulties”), political affiliation, gender, age, net worth, credit rating, occupation, presence of children in the home (yes/no), marital status, home value, and religion.
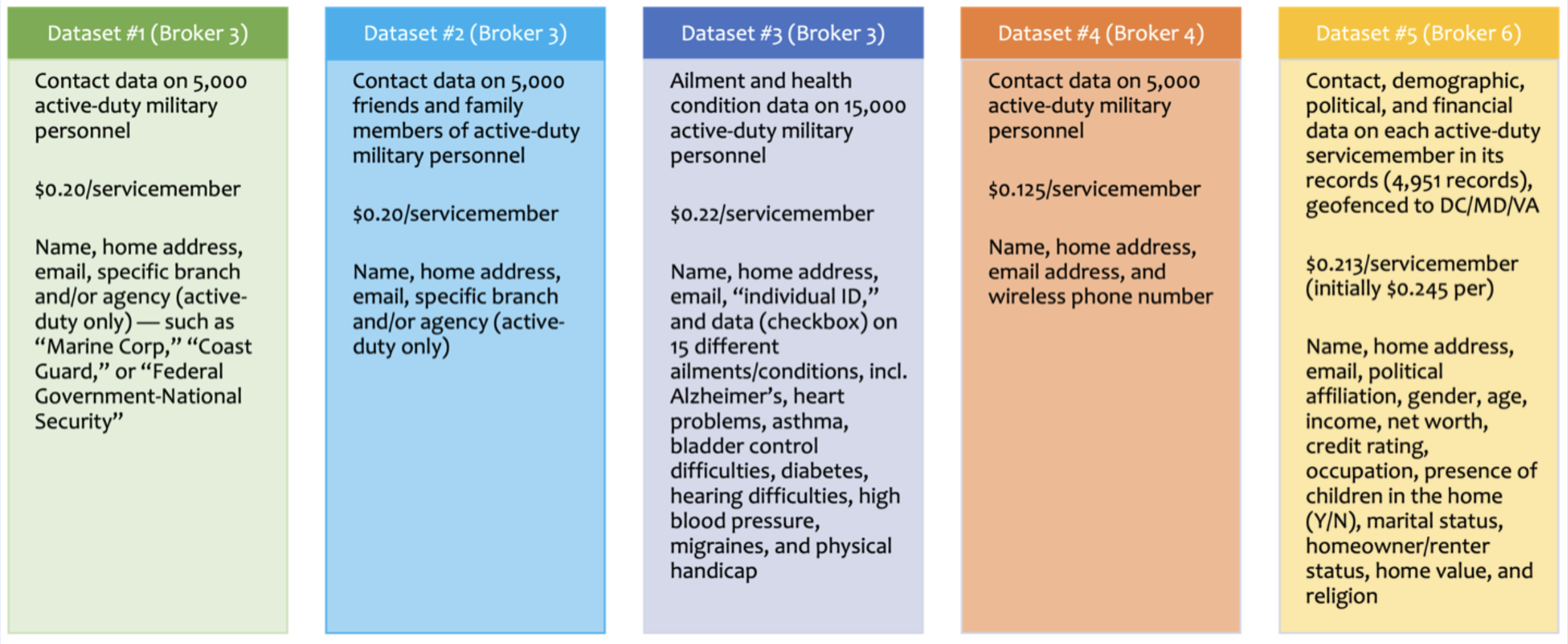
We repeated the process on the .asia side to further assess the risk that a foreign adversary could exploit the data brokerage ecosystem to get data on U.S. military personnel. We bought and set up the domain dataanalytics.asia and created a linked website with placeholder text, broad language to describe a general data research group, an explicit statement that we are affiliated with Duke University, and a disclaimer that the site was currently under construction. (We have no evidence that the brokers looked at the website.) The website was also hosted on an Amazon web server located in Singapore, giving it a Singaporean IP address. Once the website was constructed, we contacted the same data brokers from which we purchased data through the U.S. .org to see if there was any difference in the sales process and whether we would be able to purchase data on service members. We also contacted Broker 8, a location data broker, to see if we could reinitiate the purchase process through the .asia website.
All told, we purchased quite similar data from the same three data brokers on U.S. military personnel via the .asia website, without substantial vetting. Broker 3 asked no significant questions about our identity and appeared to have no barriers to selling to our .asia domain. At one point, Broker 3 asked to schedule a phone call; we declined, and it proceeded to sell us data anyway. Broker 3 also offered more data fields for purchase when we reached out via the .org (U.S.) domain (on health conditions and military branch) than it did when we reached out via the .asia domain. It is unclear if this is due to internal restrictions or because we worked with a different sales representative. Broker 4 raised some concerns at first—“you’re asking for a lot of outputs that we can only do in certain situations and we can’t see your site or vet your company and it’s a .asia domain”—but ultimately sold us a data set that included all of our requested fields except “financial [fields] like income or summarized credit.” Broker 6 never questioned our identity, attempted a phone call, or asked what we planned to do with the data, allowing us to purchase the data set quickly and easily. Similar to our experience via the U.S. domain, Broker 8, a location data broker, required a phone call and an NDA before selling data, and we did not proceed with that potential transaction.
The figure below describes the contact, demographic, financial, location, and other data we purchased via the .asia domain.
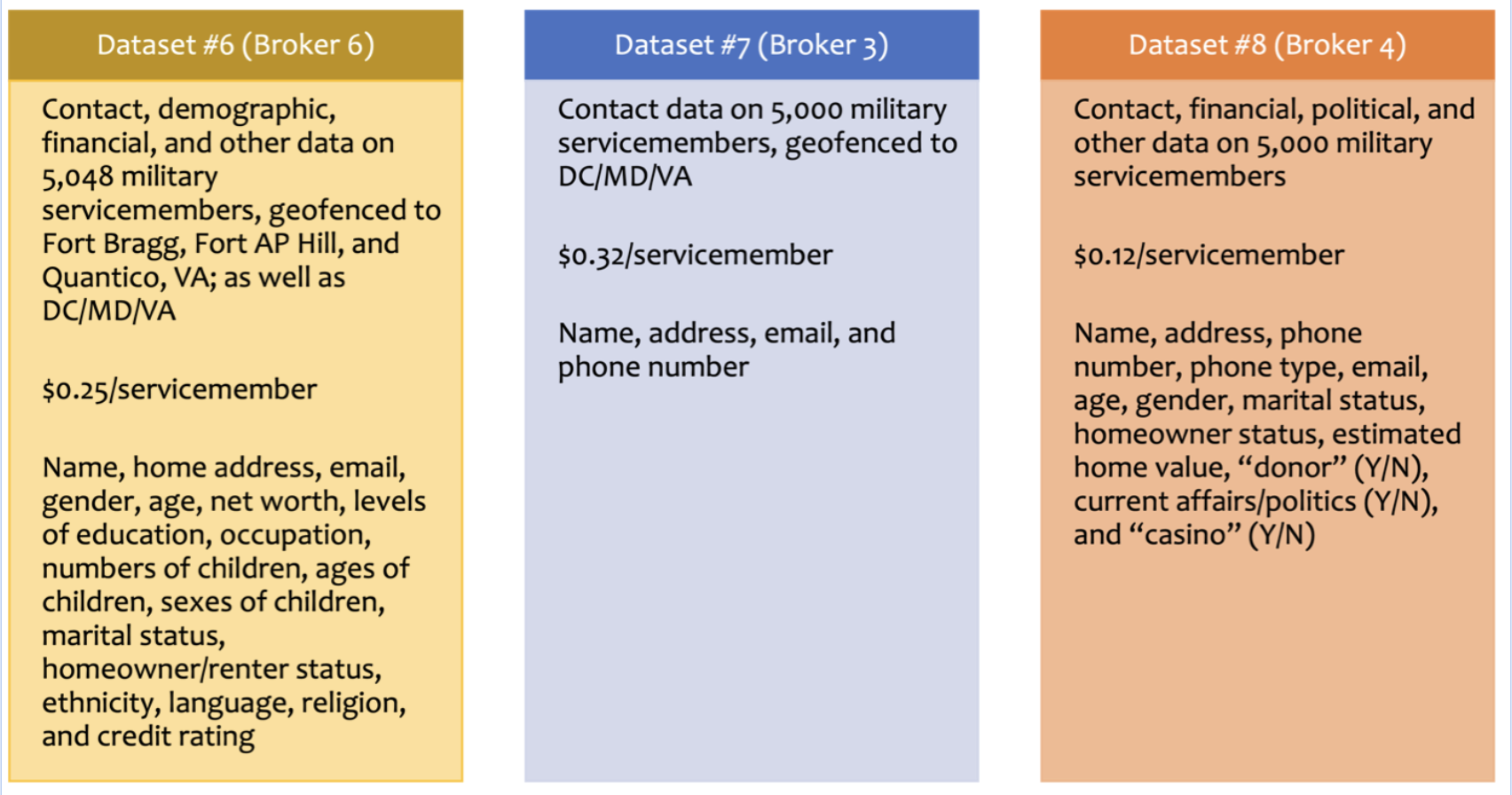
For some data sets, we also geofenced to important military and U.S. national security locations, including Fort Liberty (formerly Fort Bragg); Quantico, Virginia (home to a Marine Corps base, among other facilities); and Washington, D.C., Maryland, and Virginia. Every single data set was once again individually identified with names.
What’s to Be Done?
Data brokers gather and sell data on U.S. military personnel, including sensitive, individually identified, and nonpublic information about finances, health conditions, political beliefs, children, and religion. Simultaneously, the sale of data focused on military personnel sits within the broader, multibillion-dollar data brokerage ecosystem that gathers and sells data on virtually every single American. Our ability to purchase sensitive, individually identified, nonpublic information about military personnel with almost no vetting, including from a .asia domain, for as low as $0.12 per record, underscores the substantial risk that a foreign or malign actor could acquire this data in order to inflict harm on the U.S. military and U.S. national security. Those harmful actions could include profiling, scamming, blackmail, coercion, outing, reputation-damaging, stalking and tailing, microtargeting, and conducting other analyses on members of the national security community. To respond to these problems, regulatory agencies and the Defense Department can take some measures, but it ultimately comes down to congressional changes to U.S. privacy law.
A strong, comprehensive U.S. privacy law, with robust controls on the data brokerage ecosystem, would be the most effective step to prevent harms from data brokerage for all Americans. For example, the American Data Privacy and Protection Act (ADPPA), introduced in 2022 in the 117th Congress (not yet reintroduced in the current Congress), includes provisions to generally prohibit companies from transferring individuals’ personal data without their affirmative express consent—and to establish a centralized registry through which consumers can opt out of the sale of some of their data by some third-party data brokers. It also includes requirements for companies to implement security practices to protect and secure personal data against unauthorized access. Such provisions could introduce new controls around the collection and use of personal data about Americans, encompassing members of the U.S. military and their families.
A comprehensive privacy law should also govern the use of public records and publicly available information, which can be sources of potential harm depending on the context, and especially when aggregated by data brokers. For example, people search websites’ scraping of property filings, voting registries, and other government records enables people search data brokers to aggregate data, build profiles linked to individuals, and publish such profiles online for search and sale—including about members of the U.S. military. In a previous study, one of us was able to find profiles for sale on people search websites that appeared to correspond to the home addresses, contact information, family information, and other data of senior U.S. military figures.
Several states have passed privacy laws, including California, Colorado, Connecticut, Iowa, Virginia, and Utah. For example, the California Consumer Privacy Act gives California residents the right to delete, opt out of the sale of, and correct their data. However, the opt-out mechanism requires action by the consumer, who often is unaware their data is being collected and sold in the first place. A piecemeal state-by-state approach also allows data brokers to continue collecting data on residents of states that have not yet passed similar privacy laws. A preemptive federal privacy law would instead prevent the collection and sale of consumer data without informed and clear consent across the country and for all U.S. persons, though states would still be and are permitted to pass their own more restrictive legislation. They could also pass legislation protecting certain categories of data, akin to the Washington My Health, My Data Act (focused on health data) or the Illinois Biometric Information Privacy Act (focused on biometric data).
In addition to a comprehensive privacy law, Congress and the executive branch should consider more targeted controls focused specifically on the risks associated with data brokerage and U.S. national security. For example, data brokers could be prohibited from collecting and selling identifiable data related to government employees and active-duty service members for the purpose of sale to third parties, with a possible exception for circumstances in which it is deemed to be highly necessary, low risk, and well defined. Any targeted controls should also consider how some particularly sensitive types of data, such as location data, are at risk of compromise when widely collected and aggregated in the first place.
Beyond the legislature, the Defense Department should assess the risks from data brokerage in its contracts. This should include an internal contractual data flow assessment of how the department receives, transfers, and releases personal data about civilian employees and uniformed members of the military. The full list of data sources drawn on by data brokers is unclear but may include more official sources such as active military occupational data or privatized on-base housing information. Such an assessment may reveal opportunities to curtail the flow of sensitive military-related information to data brokers while still allowing for data flows that are necessary to military functions.
The Defense Department could also implement controls in its contracting requirements. For example, the department could reserve the right to restrict a contractor’s sale of any data, related to the contract or otherwise, to external entities throughout the contract period and restrict the future sale of data that was obtained due to the contract. The department could also mandate that contractors implement department-created screening protocols for the sale of any data, related to the contract or otherwise, to verify that any prospective data purchaser is a legitimate and non-nefarious business entity. The Pentagon could also restrict a contractor’s collection of data on current or former U.S. military personnel throughout the duration of the contract, to target the collection process that precedes inferring and selling data.
Regulatory agencies should pursue new policies, enforcement actions, and rulemaking where applicable concerning the privacy, cybersecurity, financial opportunity, and other risks associated with the data broker industry and the sale of data about military service members. The Federal Trade Commission is currently undergoing rulemaking on commercial surveillance and data security. Drawing on its authorities under Section 5 of the FTC Act—to enforce against unfair or deceptive business acts or practices—the FTC could implement rules preventing the “re-identification” of data unless the individual explicitly provided fully informed consent. Furthermore, the Consumer Financial Protection Bureau could aid in research into data brokers by asking data brokers for information about their practices to shed further light on places where regulation may be needed. Specifically, the CFPB could request information related to data streams, or the specific avenues through which brokers get their data; the prevalence and development of software development kits (SDKs) by data brokers to collect data through mobile apps; how data brokers infer data points; how data brokers re-identify seemingly “anonymous” data; and how data on military service members is collected and sold, especially credit- and financial-related data.
Congress should provide more funding to regulatory agencies to enforce any new laws or regulations related to the data broker industry and national security. To be able to investigate and enforce any resulting regulations, agencies such as the FTC and the CFPB would need sufficient resources. The FTC, for instance, lacks the resources to sufficiently carry out privacy investigations and enforcement actions, and new laws or regulations would only increase the demand for additional personnel. More funding would help to address privacy harms now and into the future, as comprehensive consumer privacy legislation is ultimately passed.
The data brokerage industry is a multibillion-dollar ecosystem. It touches everything from consumer reporting agencies; to small geolocation data brokers; to mobile apps selling their users’ information; to medium-sized enterprises offering advertising, profiling, and other services related to individuals’ data. Within that ecosystem is a large amount of data gathered, packaged, inferred, and sold about members of the U.S. military. The availability of individually identified, nonpublic, sensitive data about military service members—and the variability of controls around the collection, aggregation, and sale of the data—suggests that many risks to U.S. national security have gone unaddressed in current law, policy, regulation, and technology.
Until there are changes in the way this data is gathered, shared, analyzed, licensed, and sold, these risks will persist.






