How China’s Cyber Ecosystem Feeds Off Its Superstar Hackers

Published by The Lawfare Institute
in Cooperation With

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz. This newsletter is going on a one-week break, and the next edition will be out on June 27.
How China’s Cyber Ecosystem Feeds Off Its Superstar Hackers
A new report explores how effectively the Chinese state leverages civilian talent for state-sponsored cyber operations.
“From Vegas to Chengdu,” by Eugenio Benincasa from the Center for Security Studies at ETH Zurich, focuses on the links between Chinese hacking contests and bug bounties and the country’s cyber espionage programs. Interestingly, it finds that People’s Republic of China (PRC) vulnerability discovery efforts in recent years depend highly on just “a handful” of Chinese researchers.
The report pulls together information made public over the past several years to comprehensively summarize evidence the PRC funnels vulnerability research into state-sponsored espionage efforts.
Shortly after 2014, Chinese security researchers began dominating international hacking competitions.
The report analyzes the performance of Chinese security researcher teams at the Pwn2Own hacking competition. In 2014, Chinese teams won just 13 percent of the total prize money. By 2017, this had risen to nearly 80 percent.
Around this time, the Chinese government appears to have decided to harness its researchers’ vulnerability research capabilities for state purposes. Chinese researchers were banned from attending hacking competitions held outside the country, and in 2018 an equivalent domestic event, the Tianfu Cup, was held in Chengdu.
An iOS exploit chain published at that competition was subsequently discovered in watering hole attacks against Uyghur Muslims. Uyghurs are an oppressed minority population in the Western Chinese province of Xinjiang.
The report documents other compelling evidence that Chinese hacking competitions feed talent and exploits to state-backed cyber espionage programs.
The report says companies linked to Chinese state-sponsored cyber operations sponsor hacking competitions. Security firm Topsec, which has been linked to the 2015 breach of U.S. insurance giant Anthem, sponsors the Tianfu Cup. And the i-SOON cyber espionage contracting firm created the “Anxun Cup” hacking competition to attract talent.
i-SOON’s employees also believed that exploits from the Tianfu Cup were funneled through the provincial branches of security agencies for contractors to use in cyber operations.
The Chinese government also has regulations that mandate that vulnerability disclosure information be passed through official agencies that have links to the Ministry of State Security (see diagram below).
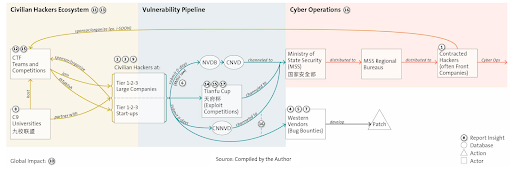
China’s Offensive Cyber Ecosystem, From Vegas to Chengdu
One benefit of this system is that it allows civilian hackers’ research to be captured for use in state programs without them being directly involved. The report provides evidence that some of China’s elite hackers have ethical standards. Accomplished hacker Qidan He (aka Edward Flanker) lost his job at Chinese e-commerce firm Pinduoduo because he refused to participate in what he described as unlawful activities. Pinduoduo’s apps were booted from the Play Store last year for using several zero-days to hack users’ devices.
We’ve heard directly from individual Chinese security researchers that they are motivated to improve global security and not by nationalistic fervor. But it is not clear what elite hackers in general think about working for Chinese national security purposes.
These elite hackers really matter. The report analyzed the contribution Chinese researchers made to Google, Microsoft, and Apple bug bounty programs, and found that a handful of individuals made an outsized contribution. For example, the report describes how credit is assigned to individuals with different research teams in the Qihoo 360 security firm:
The success of the Chinese teams is often credited to a small number of individuals. From 2017 to 2020, over 60% of vulnerabilities reported by Qihoo’s 360 C0RE to Google Android were submitted by Mingjian Zhou, either individually or in collaboration with a few additional team members. Within 360 Alpha nearly all vulnerabilities were reported by Guang Gong, whereas in 360 IceSword, over half were reported by Chen Gengjia, either individually or in collaboration with other team members. Han Zinuo contributed to over 50% of vulnerabilities reported by 360 SRC to Google Android. And in the case of Qihoo’s 360 Vulcan Yuki Chen was responsible for 68% of the team’s submitted vulnerabilities to Microsoft.
These are superstar security researchers, and their impact is reflected in vulnerability discovery numbers:
Fluctuations in a team’s contributions can often be traced back to a single individual transition between companies. This has been particularly true since 2020. For example, when Han Zinuo switched from 360 SRC to OPPO in 2020, submissions from 360 to Google Android decreased significantly, while OPPO saw a substantial increase, largely due to Han’s contributions. Likewise, when Yuki Chen moved from 360 Vulcan to Cyber Kunlun in 2020, Microsoft witnessed a significant decrease in contributions from 360 Vulcan. Cyber Kunlun meanwhile experienced a remarkable surge, with Chen being responsible for 62% of the team’s submissions to Microsoft. Sangfor experienced a significant boost when former 360 C0RE member Peng Zhiniang joined the company as a CTO in late 2020. Following Peng’s arrival, Sangfor’s vulnerabilities contributions to Microsoft surged, and the company secured third place in the Tianfu Cup 2023.
An interesting observation in the report is that the hacking targets at the 2023 Tianfu Cup shifted away from Western products toward Chinese ones. The Chinese government is trying to reduce the country’s dependency on foreign software and hardware (known colloquially as “Delete America”), so a focus on domestic software makes sense to improve its resilience.
Also, internal security is a very high priority for Chinese security services, and if targets shift to Chinese-built software, security services will follow suit. It’s a happy coincidence, then, that a focus on domestic software at the Tianfu Cup will also be useful for finding vulnerabilities that organizations like the Ministry of State Security will be able to exploit.
It is worth remembering that the two examples we have where vulnerabilities were exploited shortly after disclosure at a conference or hacking contest have targeted two of the Chinese Communist Party’s “Five Poisons”—Hong Kong pro-democracy groups and Uyghur Muslims. (Tibetans, Taiwanese, and Falun Gong are the other three.)
The report describes a fairly well integrated talent ecosystem that includes hacking contests, bug bounties, universities, private contractors, and intelligence agencies. This ecosystem is more deliberately constructed than the U.S. equivalent, which grew organically without top-down direction. It’s worth a read to understand what these ecosystems look like when the state can directly capture vulnerability research talent.
A Joint Collaborative Sense of Impending Doom
Recommendations to change the way the Cybersecurity and Infrastructure Security Agency’s (CISA’s) Joint Cyber Defence Collaborative (JCDC) works are grim news for the initiative.
The idea behind the JCDC was to “unify cyber defenders from organizations worldwide” by gathering, analyzing, and sharing actionable information. Unfortunately, that hasn’t worked out, and back in May, Politico covered a “wave of discontent” with the JCDC. One criticism was that CISA had staffed the JCDC with lawyers and policy operatives rather than technical experts. Another was that CISA’s anti-disinformation work had put the JCDC offside with conservatives, even though the JCDC did not directly deal with the subject.
Last week, The Record reported on recommendations for the JCDC issued by CISA’s Cybersecurity Advisory Committee. The recommendations address:
- The JCDC’s day-to-day activities: more operational collaboration, less policy.
- Clear criteria for JCDC membership.
- Expanded and more developed coordinating structures.
Um, so in effect these recommendations say the JCDC hasn’t got the what, the who, or the how of what it does right. And given that the JCDC’s work has become a political target, we think it better to just kill the damn thing.
Three Reasons to Be Cheerful This Week:
- Security help for hospitals from Google, Microsoft: The White House announced that Google and Microsoft would provide discounted cybersecurity services and education to U.S. rural hospitals. The assistance is welcome because these types of hospitals are in a tough spot from a cybersecurity perspective. Most rural hospitals are small with limited resources, and patients don’t have practical alternatives within a reasonable distance if operations are disrupted by a cyber incident.
- Apple launches Passwords app: Among other new security features, Apple launched a new password manager app for its operating systems at its Worldwide Developer Conference this week. Managing passwords is a thankless job for all users, so it is good to see functionality that has been hidden in Apple’s Keychain made more visible and accessible.
- FCC proposes routing security rules: The U.S. Federal Communications Commission has proposed new reporting requirements aimed at encouraging broadband providers to lift their game when it comes to the security of Border Gateway Protocol (BGP). Providers would need to prepare and update BGP security risk assessment plans and report on progress implementing RPKI-based security measures.
Shorts
Shedding Light on the Snowflake Campaign
Mandiant has released a report that sheds light on the campaign targeting Snowflake customers. Mandiant attributes the campaign to a financially motivated group it calls UNC5537, which obtained access via customer credentials captured by infostealer malware (malware that steals valuable information such as credentials or access tokens) that had infected customers’ systems. Mandiant says it “identified hundreds of customer Snowflake credentials exposed via infostealers since 2020.”
In successful compromises, multi-factor authentication was not configured, credentials had not been rotated (in some cases they were valid years after they had been stolen), and affected Snowflake instances did not have controls in place to allow only access from trusted locations.
The report said Snowflake and Mandiant had notified around 165 potentially exposed organizations to date.
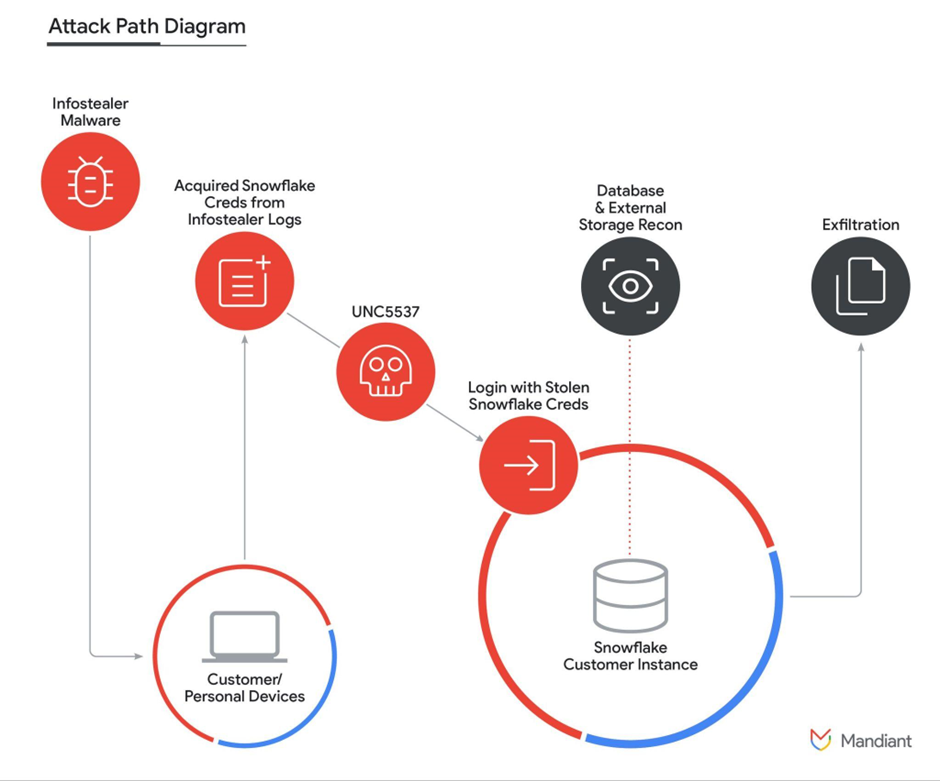
UNC5537 Snowflake attack path, Mandiant
Dutch Blow Lid on Chinese Party
Dutch military intelligence, the MIVD, has revealed that a Chinese cyber espionage campaign targeting Fortinet’s FortiGate devices is much larger than previously thought and had gained access to at least 20,000 systems worldwide. The MIVD reported on the malware used in the campaign in February when it found compromised FortiGate devices in Dutch Ministry of Defence networks. It said:
Since its publication in February, the MIVD has continued to investigate the broader Chinese cyber espionage campaign. This revealed that the state actor gained access to at least 20,000 FortiGate systems worldwide within a few months in both 2022 and 2023 through the vulnerability with the identifier CVE-2022-42475 . Furthermore, research shows that the state actor behind this campaign was already aware of this vulnerability in FortiGate systems at least two months before Fortinet announced the vulnerability. During this so-called “zero-day” period, the actor alone infected 14,000 devices. Targets include dozens of (Western) governments, international organisations and a large number of companies within the defence industry.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq talk about how the use of cyber operations in Ukraine is informative but information is incomplete. Rather than clarifying the role of cyber operations in conventional warfare, there is still a lot of room for confirmation bias.
From Risky Biz News:
Apple’s WWDC 2024 security lineup: Apple is holding its yearly Worldwide Developers Conference (WWDC) this week in Cupertino, and the company has announced several security-related features on the first day of the event.
This year’s biggest announcement is Private Cloud Compute (PCC), a new feature that will take user data and process it inside an encrypted cloud server. This feature will be used for new Apple AI services that require more processing power than is available on the user’s device. Apple says the data will be stored on servers that use custom-built hardware and run a custom operating system. Data is sent to PCC servers only with the user’s approval, and Apple says that even its staff with administrative rights can’t access or view it. Everything, of course, is wrapped in cryptographic protocols.
A technical description of this entire convoluted process is available here, and Apple says it will make PCC server software images available for security research.
Microsoft budges on Windows 11 Recall: Microsoft has cracked under the public’s pressure and is rolling out changes to its upcoming Windows 11 Recall feature. The company says Recall will ship disabled by default for all upcoming Windows 11 compatible systems. Users will be able to activate Recall only if they previously enrolled in the Windows Hello biometrics authentication system. Recall data will also be encrypted and accessible only after users have authenticated via Windows Hello. The Recall feature has been a PR disaster for Microsoft over the past month. Users have reacted negatively to the news that Recall would be taking snapshots of their screen every five seconds and storing sensitive information in an unencrypted local database. Microsoft says it made changes to Recall after feedback from its customers.
Interpol plugs Red Notices leak: Moldavian authorities have arrested four individuals suspected of sharing information about Interpol Red Notices with wanted fugitives, including cybercrime suspects.
The scheme was uncovered earlier this year by the U.K. National Crime Agency during a separate cybercrime investigation. Authorities say a criminal group paid bribes of several millions of U.S. dollars to Moldavian public servants to provide early warning of Interpol Red Notice arrest warrants.
The early warning allowed wanted individuals to seek asylum or refugee status in Moldova or other countries, a process that triggers the deletion of Red Notices from the Interpol database.
[more on Risky Business News]





