Smile! You’ve Been Sanctioned + Microsoft’s Midnight Blizzard Is Cold, Dark, and Insecure

Published by The Lawfare Institute
in Cooperation With

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on Substack.
Smile! You’ve Been Sanctioned
The Australian, U.S., and U.K. governments have upped the ante against cybercriminals by launching coordinated sanctions against a single individual involved in a significant extortion attack.
On Jan. 23, the Australian government announced financial and travel sanctions targeting Aleksandr Gennadievich Ermakov, a Russian national, for his role in the hack of Medibank Private, an Australian health insurance company.
Australia employed its cyber sanctions regime for the first time in this case. On the same day, the U.S. and U.K. governments sanctioned Ermakov.
This was a nationally significant hack that affected a meaningful proportion of the Australian population and was made worse by the hackers’ attempts to apply extra pressure by releasing sensitive information to the dark web. The more appalling releases included a file “abortions.csv” that contained more than 300 claims made by policyholders in relation to pregnancy terminations and miscarriages, and another called “boozy.csv” containing details of alcoholism-related treatment. Ultimately, all the stolen data was published.
The Australian government mounted a whole-of-government response that included the Australian Federal Police (AFP) and the Australian Signals Directorate (ASD), as well as the health and service delivery departments.
At the time, Clare O’Neil, Australia’s minister for cyber security, thanked the AFP and the ASD for the “intensive work that is underway to hunt down the attacker.”
It looks like that work paid off, and we love that the Department of Foreign Affairs and Trade released to the media a webcam photo of Ermakov.

Aleksandr Ermakov (supplied by the Department of Foreign Affairs and Trade to media outlets)
Russian law enforcement action against cybercriminals in these types of cases just doesn’t happen, so coordinated sanctions are one of Western governments’ better options.
In 2019, the U.S. sanctioned Evil Corp, and, in 2023, the U.S. and U.K. sanctioned 18 members of the TrickBot gang in two different tranches over the course of the year.
In addition to the direct effects of sanctions on individuals, such as curtailing financial options and travel destinations, sanctions also appear to affect cybercrime business prospects. Victims are reluctant to pay sanctioned individuals or groups, and, as a result, other criminals avoid being associated with these entities.
At the Australian press conference announcing the sanctions, Abigail Bradshaw, head of the Australian Cyber Security Centre, pointed out that “cybercriminals trade in anonymity.”
“It is a selling quality, and so naming and identifying with the confidence that we have from our technical analysis will most certainly do harm to Mr Ermakov’s cyber business,” she continued.
We don’t think sanctions against criminals will “solve” cybercrime but should be applied to deter the worst behavior. Given that there is really a lot of unacceptably bad behavior going around, more sanctions is good news.
Microsoft’s Midnight Blizzard: Cold, Dark, and Insecure
Microsoft’s latest security clanger is, well, unbelievable.
Late last Friday, Microsoft revealed that it had been successfully compromised by a group it calls Midnight Blizzard. This group has been attributed by the U.S. and U.K. governments to Russia’s foreign intelligence service, the SVR.
A single paragraph from Microsoft’s announcement contains all the important details:
Beginning in late November 2023, the threat actor used a password spray attack to compromise a legacy non-production test tenant account and gain a foothold, and then used the account’s permissions to access a very small percentage of Microsoft corporate email accounts, including members of our senior leadership team and employees in our cybersecurity, legal, and other functions, and exfiltrated some emails and attached documents. The investigation indicates they were initially targeting email accounts for information related to Midnight Blizzard itself. We are in the process of notifying employees whose email was accessed.
The company then had the cojones to write “the attack was not the result of a vulnerability in Microsoft products or services.” This is technically correct, in that none of Microsoft’s systems had a formal cybersecurity vulnerability or CVE. But it makes sense only if you speak cyber jargon and not English and think that “absence of security” is not a vulnerability.
In this incident, Midnight Blizzard took advantage of a string of Microsoft security failures to achieve their apparent goals: A test account was given extensive permissions that weren’t removed after testing was completed; the account was not protected from basic password spraying attacks; and the account was not deactivated when testing was finished.
U.S. Sen. Ron Wyden (D-Ore.) told CyberScoop that “this is yet another wholly avoidable hack that was caused by Microsoft’s negligence.”
We’ve written before about Microsoft’s subpar security culture. In announcing this incident, the company wrote:
For Microsoft, this incident has highlighted the urgent need to move even faster. We will act immediately to apply our current security standards to Microsoft-owned legacy systems and internal business processes, even when these changes might cause disruption to existing business processes.
This will likely cause some level of disruption while we adapt to this new reality, but this is a necessary step, and only the first of several we will be taking to embrace this philosophy.
Well, duh. Microsoft finally seems to be realizing that to improve its own security it might need to prioritize it over some of its other efforts. When Microsoft announced its Secure Future Initiative late last year, this kind of language that elevated security was entirely missing and was the key reason we were underwhelmed by the launch of Microsoft’s “security reset.”
These paragraphs contain the right message, but it’s disappointing that this message is coming from the relative backwater of the Microsoft Security Response Center rather than, say, CEO Satya Nadella, President Brad Smith, or even Security Vice President Charlie Bell. Microsoft is being dragged kicking and screaming to actually reprioritize security, one awful breach at a time.
SEC Disclosure: How Much Is Too Much?
Microsoft’s decision to disclose the Midnight Blizzard breach to the U.S. Securities and Exchange Commission (SEC), without determining the incident’s material impact, may prompt a surge of nonmaterial cybersecurity disclosures. Whether this is actually an issue depends on the perspectives of stakeholders in this process.
While some company cybersecurity leaders argue Microsoft’s decision will clutter the SEC channel and increase the burden on companies of preparing disclosure announcements, the SEC and industry observers believe more cybersecurity incident disclosure is vital.
On Dec. 18, 2023, a new SEC rule on the disclosure of material cybersecurity incidents came into effect. This rule requires that companies inform the market within four days once they’ve determined that a cybersecurity incident is material. In this rule, the SEC says information is material:
if “there is a substantial likelihood that a reasonable shareholder would consider it important” in making an investment decision, or if it would have “significantly altered the ‘total mix’ of information made available.” “Doubts as to the critical nature” of the relevant information should be “resolved in favor of those the statute is designed to protect,” namely investors. [Ed: quotes here reference various court cases]
In its SEC disclosure, filed on Jan. 19, Microsoft writes that “the incident has not had a material impact on the Company’s operations” and it “has not yet determined whether the incident is reasonably likely to materially impact” the company’s financial results or operations.
One CISO we spoke to said, “I guess Microsoft is acting the way we’d expect but it’s just confirming the bummer of a new world we’re in.”
“Companies will be filing 8-Ks all over the place and cluttering up the SEC channel with non investor-relevant crap,” he added. (Ed: 8-Ks are the SEC form used to disclose significant events)
“The burden to get an 8-K out is enormous and has a long tail of cost and follow up headache so makes the burden of transparency very expensive. And now that Microsoft went first we’re even more committed as an industry to the emerging precedent.”
However, Microsoft is not the only company erring on the side of transparency. Even before Microsoft’s disclosure, on Dec 29, 2023, First American Financial Corporation disclosed a cybersecurity incident despite not yet having determined that it would be material.
In its disclosure, the company wrote that it “continues to assess whether the incident will have a material impact on the Company’s financial condition or results of operations, which at this point cannot be determined.”
For the SEC, the underlying drivers that require stronger disclosure requirements are that, in the words of Erik Gerding, its director of corporation finance, “disclosure practices have remained inconsistent,” while “cyber security risks have increased alongside the ever-increasing share of economic activity that depends on electronic systems.”
That seems fair enough. Of course, we’d rather see companies spend money getting security right rather than on disclosure statements that jump the gun.
Flying High: What Critics of the CSRB Get Wrong
As U.S. lawmakers consider whether to permanently establish the Cyber Safety Review Board (CSRB), a U.S. Senate hearing has raised questions about how it operates.
Some criticism has focused on the extensive private-sector involvement in the board and the potential for conflicts of interest to arise. The current board is half senior federal government cybersecurity officials and half cybersecurity luminaries from the private sector and academia. Another point of criticism is that all CSRB members have full-time day jobs.
In our view, the CSRB’s mixed public-private composition is absolutely necessary to have any impact in today’s cybersecurity environment.
The CSRB has so far produced two excellent reports that have examined systemic issues and are unique because they try to identify root causes and develop recommendations that directly address them.
Its first review looked at the Log4Shell vulnerability and supply chain security more generally, and, based on our Seriously Risky Business high-level summary, found “supply chain security is massively underdone.” The second report looked at the outrageous success of Lapsus$-style hackers, with our summary being that “current cyber security practices are ineffective against a new breed of hackers.”
The CSRB is often compared with the National Transportation Safety Board (NTSB), the U.S. agency that investigates transport accidents and issues safety recommendations aimed at preventing future disasters.
There are, however, massive differences between how NTSB accident investigations flow through to action in the transportation sector and how recommendations from the CSRB are converted into action.
In a recent Boeing 737 incident, for example, NTSB discoveries resulted in the Federal Aviation Administration grounding aircraft and ordering operators to inspect specific bolts. The problem is discrete, there are a relatively small number of stakeholders, and regulators have authorities that ensure compliance.
None of that exists in the cybersecurity space. The problems are broad, there are usually large numbers of stakeholders, and regulators have limited clout.
In our view, without private-sector involvement, a newly constructed independent government body simply won’t get the traction it needs to make a dent in current cybersecurity problems. The CSRB really needs a lot of credibility and reach to have any kind of impact in the current environment.
In an interview with Patrick Gray and Adam Boileau on this week’s edition of the Risky Business podcast, CSRB Chair Rob Silvers said the board’s composition “gives the board a lot of credibility to drive change.”
“And when those people come together and speak as to what needs to happen out there, what CISOs need to do, what network defenders need to do, what regulators need to do, what legislatures need to do, that speaks with incredible force and cannot be replicated by a government only enterprise,” he continued.
Given that, other issues that critics raise, such as potential conflicts of interests, recusal processes, and the careful application of subpoena powers, need to be managed. Silvers discusses how these processes are either already in place or have been thought through in potential legislation. They are also examined here in Politico.
Three Reasons to Be Cheerful This Week:
- iPhone Stolen Device Protection: Apple rolled out what it is calling “Stolen Device Protection” in its iOS 17.3 release this week. It’s a measure that adds extra protections to help stop thieves from capturing the entirety of your digital life if they steal your phone and learn your passcode. This will occur to only a minority of people, but it is good that Apple is still improving protections for what could be considered edge cases.
- CISA’s ransomware warnings: In its 2023 Year in Review, CISA says it issued 1,200 “pre-ransomware” warnings that alert organizations of early-stage ransomware activity on their networks. This potentially enables the affected organization to head off a full-on ransomware attack. More coverage at Cybersecurity Dive.
- Second FTC geolocation data broker win: The Federal Trade Commission (FTC) announced its second settlement with a geolocation data broker this week. As with its win last week, the FTC’s complaint relies on the data broker, InMarket, not properly getting informed consent from consumers.
Shorts
Using Facial Recognition on Faces Predicted From DNA Is a Disaster
This Wired article recounts one police department’s attempt to use facial recognition technology on a virtual face as imagined from DNA information collected at a crime scene. This newsletter supports use of facial recognition technology when it makes sense and with appropriate checks and balances. But this is disastrous.
U.K. Post Office’s Tragic Horizon Failure
This Ars Technica article covers the tragic tale of bugs in the Horizon software system that was installed in U.K. post offices from 1999 to 2015. These bugs resulted in faulty accounts that were then used to justify the prosecution and conviction of more than 900 U.K. Post Office employees.
Stablecoins the Sanction Evasion Crypto of Choice
Blockchain analysis company Chainalysis has found that stablecoins, cryptocurrencies pegged to something stable like the U.S. dollar, are the vehicle of choice for crypto scammers and entities trying to avoid sanctions. Makes sense. Why add currency valuation risk to your problems when you are just trying to make a dishonest living?
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq talk about data brokers and how having so much data available about Americans feels creepy, yet there is little visible harm to individuals. But there are still reasons to be worried.
From Risky Biz News:
CISA director swatted: CISA Director Jen Easterly was the target of a swatting attempt on the night of Dec. 30, 2023, according to a report from The Record, citing sources inside CISA. The attacker claimed gunfire was heard from Easterly’s house. The CISA official was unharmed after Arlington County Police arrived on scene and determined no shooting had occurred. The incident comes as a large number of U.S. officials have been swatted over the past weeks, with two incidents targeting the White House itself.
GVSU hack: A Ukrainian hacker group named BlackJack has breached and wiped more than 150 systems belonging to the Main Military Construction Directorate for Special Facilities (GVSU), a state-owned company that builds military facilities for the Russian military. The group claims it also downloaded more than 1.2 terabytes of information from the company’s servers containing information on more than 500 military objectives. The BlackJack group has been informally linked to the Security Service of Ukraine. Ukraine’s Main Directorate of Intelligence, or GUR, praised the attack on Telegram as a major success. [Additional coverage in UkrInform/English coverage in BusinessInsider.]
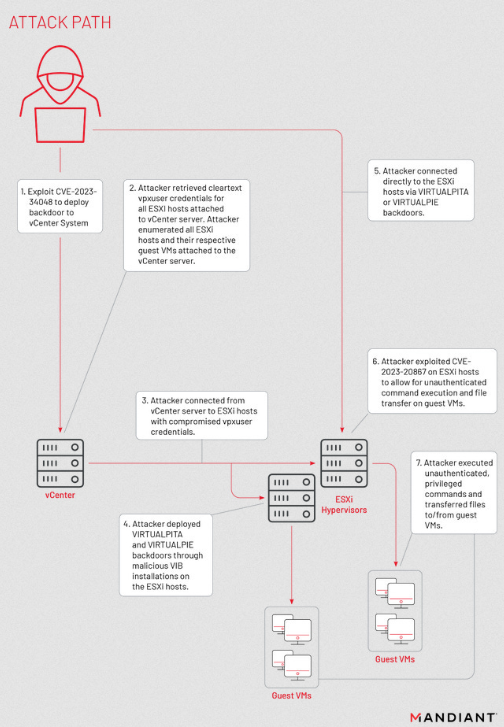
UNC3886: Google’s Mandiant division says that a VMWare vulnerability patched in October 2023 was secretly exploited in the wild by Chinese hackers since late 2021. Mandiant linked the attacks to a group it tracks as UNC3886. The group has a long history of going after devices that cannot run EDR security products, allowing their attacks to go undetected for longer. When it patched the vulnerability (CVE-2023-34048) in October, VMWare wasn’t aware of active exploitation but released patches even for end-of-life devices.


.png?sfvrsn=4156d4f8_5)
-(1)-(1).png?sfvrsn=1bc11cd_4)

