The Microsoft Breach That Won’t End + Does Delete America Mean Delete China?
The latest edition of the Seriously Risky Business cybersecurity newsletter, now on Lawfare.

Published by The Lawfare Institute
in Cooperation With

The Microsoft Breach That Won’t End
The Russian Foreign Intelligence Service (SVR)-linked group that initially breached Microsoft in November is still accessing the vendor’s systems.
Microsoft originally disclosed the breach in late January and attributed it to a group it calls Midnight Blizzard, which has been linked to Russia’s SVR by the U.S. and U.K. governments.
Last Friday, Microsoft announced in a blog post and SEC filing that Midnight Blizzard was continuing to gain access to Microsoft systems, including “some of the company’s source code repositories and internal systems.” Microsoft writes:
It is apparent that Midnight Blizzard is attempting to use secrets of different types it has found. Some of these secrets were shared between customers and Microsoft in email, and as we discover them in our exfiltrated email, we have been and are reaching out to these customers to assist them in taking mitigating measures. Midnight Blizzard has increased the volume of some aspects of the attack, such as password sprays, by as much as 10-fold in February, compared to the already large volume we saw in January 2024.
The “secrets” Microsoft refers to could include API keys, access tokens, or passwords.
The vendor notes that “to date we have found no evidence that Microsoft-hosted customer-facing systems have been compromised.”
That’s a curious turn of phrase, and we wonder if this implies that customer-hosted and/or non-customer-facing systems have been compromised instead? Is that too cynical?
The initial breach involved a string of security failures that reminded us of the compromise of Microsoft’s email services by a Chinese state-sponsored actor last year. The take-home message from these incidents was that Microsoft’s security culture wasn’t up to scratch.
These breaches are turning into a case study of why security should be a long-term strategic priority for a vendor building a cloud environment. In Microsoft’s case, yoloing security decisions may have allowed the vendor to roll out its cloud services more rapidly, but it has accrued a substantial “security debt.”
Microsoft is now trying to evict intruders from a cloud environment proved to have bizarre and unexpected vulnerabilities that shouldn’t exist in theory, but do in practice. What a nightmare.
Does Delete America Mean Delete China as Well?
Last week, the Wall Street Journal reported on a Chinese government directive to reduce the country’s reliance on American technology. The directive, known as Document 79, or colloquially as “Delete A” for “Delete America,” was issued in September 2022 but has only now been reported. Per the Wall Street Journal:
Document 79 was so sensitive that high-ranking officials and executives were only shown the order and weren’t allowed to make copies, people familiar with the matter said. It requires state-owned companies in finance, energy and other sectors to replace foreign software in their IT systems by 2027.
The directive appears to be more about self-sufficiency rather than security per se, but it highlights the asymmetry of Chinese companies operating more or less freely in America while U.S. companies are effectively banned or disadvantaged when it comes to operating in the People’s Republic of China (PRC).
In addition to economic unfairness, the behavior of Volt Typhoon also highlights security concerns about U.S. reliance on Chinese products for critical functions. This PRC-sponsored group appears to be preparing to disrupt U.S. critical infrastructure in the event of a military conflict.
If the PRC is prepared to pull the trigger in U.S. critical infrastructure, why wouldn’t it take advantage of Chinese-made products in critical sectors to add to the chaos?
One sector where this is already playing out is in logistics. In February, the Biden administration announced plans to strengthen the cybersecurity of U.S. ports and spend $20 billion to replace Chinese-made cranes.
Another sector that is affected by this dynamic is social media. If the PRC is preparing to disrupt critical infrastructure, why wouldn’t it take advantage of TikTok?
On March 13, the U.S. House of Representatives passed a bipartisan bill that would require TikTok to separate itself from its Chinese parent company ByteDance or face a ban.
The bill itself—the Protecting Americans from Foreign Adversary Controlled Applications Act—doesn’t ban TikTok outright but essentially prevents U.S. app stores from distributing or updating the app. Even though TikTok and its parent are specifically named in the bill, it isn’t aimed solely at the company. The bill also encompasses any “adversary controlled application” with more than a million monthly active users, where adversaries are defined as the PRC, Russia, North Korea and Iran.
This isn’t the first U.S. government action against ByteDance and TikTok. In August 2020, President Trump ordered that ByteDance sell its U.S. assets, but this order was struck down in court. Some action seemed possible in the early days of the Biden administration, but Democrats feared alienating younger voters prior to this year’s presidential election.
U.S. social media is not allowed to operate in China, so there was always an argument for reciprocal treatment of PRC-controlled applications in the United States. Unlike 2020, this is now coupled with knowledge of the broader Chinese government policy to “Delete America” and an understanding that the PRC is building its capability to disrupt U.S. critical infrastructure.
Even though Biden’s reelection campaign joined TikTok in February, the White House is backing the legislation.
AlphV’s Dead Cat Bounce
After being disrupted by the FBI in mid-December, the AlphV aka BlackCat group struck back with a Feb. 21 attack on Change Healthcare. But what does this tell us about the effectiveness of law enforcement disruption operations?
Here is a short summary of significant events:
- In mid-December, the U.S. Department of Justice announced it had disrupted the AlphV group. The department said it had seized several websites, gained visibility into the group’s computer network, and developed a decryption tool that would help affected victims restore their systems.
- AlphV’s administrator responded by encouraging affiliates to attack the health care sector.
- On Feb. 21, AlphV struck back with an attack on Change Healthcare. This attack resulted in what the American Hospital Association called “the most significant and consequential incident of its kind against the US healthcare system in history.”
- On March 1, $22 million was paid to AlphV, which some commentators suspect was a ransom payment from Change Healthcare.
- By March 5, the AlphV group appears to have absconded with the money without paying the affiliate directly responsible for the attack. This “exit scam” spells the end of AlphV as an active group.
- As of March 12, the U.S. health system was still struggling with payment problems.
Now, you could look at this sequence of events and conclude the AlphV takedown was ineffective, but we think that’s the wrong take. The heat from the FBI undoubtedly factored in to AlphV’s decision to pull the plug and run off with its affiliate’s money. AlphV’s “brand” among affiliates is now permanently dead, but without that law enforcement pressure, the group may well have decided to continue operating.
Three Reasons to Be Cheerful This Week:
- Incognito Market exit scams and extorts participants: Incognito Market, a darknet narcotics market, has begun extorting buyers and sellers with the threat of releasing cryptocurrency transaction and chat records. The extortion fee ranges from $100 to $20,000 and comes shortly after an exit scam in which administrators took funds that market participants had placed in the platform. Krebs on Security has an entertaining write-up of these events.
- $10 million in bug bounties: Google has published a review of its 2023 Vulnerability Reward Program, in which over 600 researchers in 68 countries received around $10 million in awards.
- Malta to strip citizenship from Intellexa CEO: The Maltese government has started the process to revoke the citizenship of Tal Dilian, the founder and CEO of spyware manufacturer Intellexa. The U.S. Treasury Department last week sanctioned Dilian and his company. The Malta Independent has more coverage.
Shorts
CISA’s Ivanti Pwnage
The Record reports that two U.S. Cybersecurity and Infrastructure Agency (CISA) systems were taken offline last month after they were breached via vulnerabilities in Ivanti products.
CISA told The Record that these systems were immediately taken offline and that there was no ongoing operational impact.
This incident underscores many of the reasons corporate cybersecurity is difficult. It’s hard to know which products are secure, and it can be hard to remediate them quickly when they are found to have vulnerabilities. The key, as CISA points out, is to have an incident response plan in place.
The CISA Ivanti compromise took place in early February. On the 29th of that month, CISA issued an advisory that essentially said that tools Ivanti provided to detect compromise didn’t work reliably, threat actors could gain root-level persistence despite issuing factory resets, and it came as close as it could to recommending that organizations decommission the products.
In this case, CISA is preaching what it practices.
When Your Car Is a Snitch
The New York Times describes how car companies monitor consumers’ driving behavior and pass that information on to be used by the insurance industry. One owner of a Chevrolet Bolt obtained his “consumer disclosure report” from the LexisNexis data broker, and, per the New York Times:
What it contained stunned him: more than 130 pages detailing each time he or his wife had driven the Bolt over the previous six months. It included the dates of 640 trips, their start and end times, the distance driven and an accounting of any speeding, hard braking or sharp accelerations. The only thing it didn’t have is where they had driven the car.
On a Thursday morning in June for example, the car had been driven 7.33 miles in 18 minutes; there had been two rapid accelerations and two incidents of hard braking.
Unsurprisingly, it is hard for consumers to know what is going on under the hood of these schemes.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq look at recent efforts to disrupt ransomware gangs and discuss what could make these efforts more effective.
From Risky Biz News:
Crypto-fraud is now bigger than business email compromise (BEC): The FBI has published its yearly Internet Crime Report [PDF], and the main takeaway from this year’s edition is that Americans are really bad at spotting cryptocurrency-themed investment scams.
For the first time since the FBI started putting out its yearly report in the early 2010s, last year, Americans lost more money to crypto-investment scams than all BEC incidents combined.
Americans lost $4.57 billion to investment scams last year, of which $3.94 billion was linked to crypto schemes.
Losses related to BEC attacks accounted for $2.94 billion, a full $1 billion below the crypto-fraud number—marking the first time this has ever happened.
[more on Risky Business News]
Tor launches new WebTunnel anti-censorship protocol: The Tor Project has launched this week a new anti-censorship tool named WebTunnel.
WebTunnel is a new type of Tor bridge, a type of secret server that is not listed in Tor’s public directory.
Because they are not public, Tor bridges are typically used in oppressive countries to allow users to connect to the Tor network.
[more on Risky Business News, including how this is another step in the back and forth between web censors and Tor, and how WebTunnel makes Tor traffic look like other HTTPS connections.]
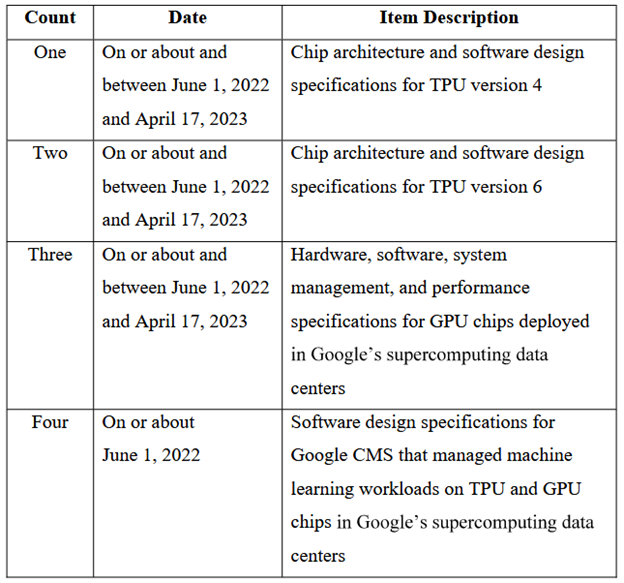
Google engineer charged: The U.S. Justice Department has charged a Google engineer with allegedly stealing the company’s artificial intelligence (AI) trade secrets. Officials have identified the suspect as Linwei Ding, a Chinese national living in Newark, California. Ding was detained this week after allegedly transferring more than 500 confidential files on Google’s AI technology to his personal account. The secret thefts happened between May 2022 and May 2023. U.S. officials claim Ding was planning to hand over the stolen Google technology to two Chinese AI startups. According to court documents, he was chief technology officer at one of the companies.