The Three I's In Spyware

Published by The Lawfare Institute
in Cooperation With

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz.
The Three I’s In Spyware
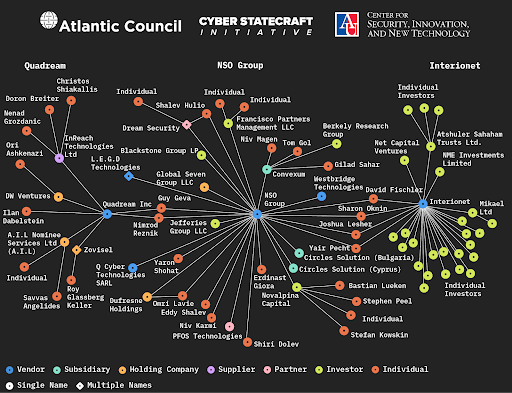
A new report finds the global spyware market is concentrated in Israel, India, and Italy and that a few individuals have founded a number of spyware vendors. Mythical Beasts and Where to Find Them, from the Atlantic Council’s Digital Forensics Research Lab (DFRLab), attempts to map the global spyware market and identify links between firms, based on public reporting coupled with searches of corporate registries and databases.
DFRLab found information on:
forty-nine vendors along with thirty-six subsidiaries, twenty-four partner firms, twenty suppliers, and a mix of thirty-two holding companies, ninety-five investors, and one hundred and seventy-nine individuals, including many named investors.
Nearly 44 percent of the entities in the data set clustered in Israel, including eight vendors (NSO Group, SaitoTech—formerly Candiru Ltd, Cognyte, Paragon Solutions, MerlinX, Quadream Inc./InReach Technologies Limited, Blue Ocean Technologies, and Interionet).

Connections between NSO Group, Quadream, and Interironet. Source: DFRLab
Clusters in India and Italy are not as large, although they’re similarly interconnected. DFRLab found vendors often changed names and identities and that significant cross-border capital flows funded the industry.
The report is realistic that spyware is “dual use”:
State surveillance, harassment, repression, and outright murder predate spyware, and there is little to suggest spyware “causes” these abuses. Measuring the human rights harms and national security risks of spyware against its value to law enforcement or intelligence activities is also challenging as these activities are, by their nature, even less visible. Few governments have sought to demonstrate the range of legitimate uses of spyware or its impacts. As a result, when considering spyware’s effects on society, there is a bias to what is known.
The report’s recommendations focus mostly on increasing transparency including requirements to “know your vendor” when buying spyware, improving information in corporate registries and improving the robustness of export licensing processes. Even if fully implemented, these recommendations won’t “fix” abusive spyware, but they are positive and realistic suggestions for improvement.
Tenet Interference Is the Tip of the Iceberg
A barrage of U.S. government actions are exposing a sophisticated media influence and interference system controlled by the Russian government. However, the measures just scratch the surface of malign foreign influence efforts. Our sister newsletter, Risky Business News, has a comprehensive breakdown of the U.S. actions announced last week, which tackle different “layers” of Russia’s disinformation system, each of which performs different functions.
One initiative involved taking down 32 domains used to host Kremlin propaganda on sites that mimicked legitimate news brands. This disinformation campaign has been previously reported as “Doppelganger.” The Department of Justice linked this campaign to senior Russian officials:
As alleged in an unsealed affidavit, the Russian companies Social Design Agency (SDA), Structura National Technology (Structura), and ANO Dialog, operating under the direction and control of the Russian Presidential Administration, and in particular First Deputy Chief of Staff of the Presidential Executive Office Sergei Vladilenovich Kiriyenko, used these domains, among others, to covertly spread Russian government propaganda with the aim of reducing international support for Ukraine, bolstering pro-Russian policies and interests, and influencing voters in U.S. and foreign elections, including the U.S. 2024 Presidential Election.
On the same day, the Justice Department indicted two RT employees (RT is a state media outlet formerly known as Russia Today) that it alleges secretly paid a U.S.-based online media company to produce content that promoted Russian interests and narratives. The indictment alleges RT employees Kostiantyn Kalashnikov and Elena Afanasyeva used fake personas to pay a Tennessee-based company $10 million to create content for social media. The U.S. company, which media reports have identified as Tenet Media, is alleged to have paid some right-wing influencers around $100,000 per video. The Justice Department says that Kalashnikov and Afanasyeva exerted significant creative control at what the indictment calls “US Company-1”:
In order to carry out RT’s secret influence campaign in the United States, Kalashnikov and Afanasyeva operated under covert identities at U.S. Company-1. Posing as an outside editor, Kalashnikov edited U.S. Company-1 content, monitored U.S. Company-1’s funding and hiring, and introduced Afanasyeva as a member of his purported editing team. Using the fake personas Helena Shudra and Victoria Pesti, Afanasyeva posted and directed the posting by U.S. Company-1 of hundreds of videos. Afanasyeva also collected information from and gave instructions to U.S. Company-1 staff. For example, after the March 22, 2024, terrorist attack on a music venue in Moscow, Afanasyeva asked one of U.S. Company-1’s founders to blame Ukraine and the United States for the attack, writing: “I think we can focus on the Ukraine/U.S. angle. ... [T]he mainstream media spread fake news that ISIS claimed responsibility for the attack yet ISIS itself never made such statements. All terrorists are now detained while they were heading to the border with Ukraine which makes it even more suspicious why they would want to go to Ukraine to hide.”
Most of the influencers connected to Tenet Media have denied being aware that Russia or RT was the source of the funds. The indictment alleges the company’s founders misled at least two of Tenet’s commentators by creating a fictional Belgian investor.
The U.S. government also linked RT to Russian intelligence services. In its statement announcing sanctions in response to malign foreign influence operations, the U.S. Treasury stated that RT’s deputy editor-in-chief, Anton Sergeevich Anisimov, “conducts activities on behalf of the Russian Federal Security Service (FSB).”
The U.S. government also took aim at the pro-Kremlin purported hacktivist group RaHDit (Russian Angry Hackers Did It). The State Department issued a $10 million reward, and the Treasury also sanctioned three members. Treasury’s statement says:
Aleksey Alekseyevich Garashchenko (Garashchenko) is the head of RaHDit and was an FSB officer at the time he started leading the group. Garashchenko directly interacts with members of the Russian intelligence and security services, members of the Russian Presidential Administration, and employees from RT.
The State Department says RaHDIt “has previously engaged in election influence in other countries and is a threat to the 2024 U.S. elections, particularly through cyber-enabled influence operations.”
Although Doppelganger, RT’s covert influence over domestic commentators, and RaHDit all perform separate functions, they are part of a larger disinformation or propaganda system.
For example, RaHDit and Doppelganger can hack or falsify material, respectively. Domestic commentators could then amplify and “launder” or lend credibility to the material, as per standard Russian tactics, so that the narrative Russia favors takes root in mainstream discourse.
Although the U.S.’s actions address a range of Russian activities and link them to the Russian government, these actions just show us the tip of the iceberg.
When it comes to RT’s covert efforts, for example, the indictment says Kalashnikov manages “multiple covert distribution channels in the United States.” That makes sense to us. It’s inconceivable that a program to co-opt American influencers to disrupt a presidential election focuses on a single U.S. company and is run solely by a 31-year-old deputy chief (Kalashnikov) with some help from his 27-year-old producer (Afanasyeva).
The U.S. government also released documents and project proposals relating to the Doppelganger campaign. These documents contain goals such as to “to secure victory” for a particular candidate in the 2024 U.S. presidential election and “to increase the percentage of Americans who believe that the U.S. ‘has been doing too much to support Ukraine’ to 51%.” They suggest, without confirming, that a broader range of activity is taking place.
Although the sanctions, indictments, and rewards the U.S. government has announced probably won’t reap direct results soon, collectively they have tremendous educational value. This alerts influencers and journalists to the possibility that foreign manipulation comes with buckets of money.
This story in Semafor, for example, describes a similar situation in which an influencer network was paid to promote misogynistic smears involving Vice President Kamala Harris. Although the incident occurred in July, the article was published shortly after the recent U.S. actions were announced. This network was organized over Zoom calls and email and payments made on the Zelle platform. But participants did not identify themselves by name, and cameras were switched off during video calls. A bit weird, and Semafor says “the money was good: One participant made more than $20,000 for several weeks of boosting assigned messages, according to the Zelle receipts.”
To us, this amount of money is surprising, but perhaps this is normal? Per Semafor:
Leading figures in the booming conservative influencer industry, meanwhile, said that the size of payments seemed consistent with their business—but said they’d never heard of this operation.
Compared to tracking money flows through front companies, countering manipulation on most social media platforms is easy given those companies have deep visibility of what occurs on their platforms. Because they can see all sorts of technical and behavior patterns, they can successfully clamp down on unwanted behavior. We’ve seen Russia move away from Meta properties, but some social media companies seem less motivated to tackle Russian propaganda.
The opposite applies to influencers, front companies, and money flows.
The RT indictment notes that earlier this year RT’s editor-in-chief spoke on Russian television of “an enormous network, an empire of covert projects that is working with the public opinion, bringing truth to Western audiences.” Which leaves us wondering, just how much is Russia spending on this election?
Three Reasons to Be Cheerful This Week:
- Terrorgram Collective leaders arrested: The U.S. Department of Justice announced it had arrested and charged two leaders of a transnational terrorist group that organized on Telegram. It is alleged the pair promoted a white supremacist ideology and solicited hate crimes including the shooting of three people outside an LGBTQI+ bar in Slovakia and the stabbing of five people near a mosque in Turkey.
- Durov pledges to improve moderation: Telegram’s CEO, Pavel Durov, said he would “significantly improve” moderation on the messaging app, just a week after being charged with complicity in crimes facilitated over Telegram. The service also removed multiple channels hosting explicit deepfake material of South Korean women and apologized for its late response to the police request to do so.
- CISA steps away from content moderation: CyberScoop says that Jen Easterly, director of the U.S. Cybersecurity and Infrastructure Security Agency, told reporters last week that the agency would no longer flag misleading election information to social media platforms for content moderation or removal. The practice became politically controversial, and any benefit gained simply wasn’t worth the political grief.
Shorts
The $10 Million Self-Licking Ice Cream
Michael Smith, a North Carolina man, has been charged by the U.S. Department of Justice with music streaming fraud that earned him over $10 million in royalties. The department alleges Smith earned unlawful royalties by using bots to generate billions of streams from hundreds of thousands of AI-generated songs Smith uploaded to streaming platforms such as Apple Music, Amazon Music, and Spotify. Although stealing from Apple or Amazon may seem like a victimless crime, the indictment says that streaming services generally pay a percentage of revenue to rights holders. So streaming fraud doesn’t hurt the platforms but instead diverts funds from legitimate songwriters and musicians.
When Phishing Is Deadly
Ukraine’s CERT has warned that hackers are targeting Ukrainian defense personnel with Signal messenger links that appear to point to military systems mobile apps. The links contain malware or malicious code intended to steal credentials to access military systems and gather the GPS coordinates of the device. The CERT notes the “attacks are extremely dangerous and may have direct negative consequences for the life and health of military personnel.”
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq dissect an FBI advisory about North Korean groups targeting cryptocurrency firms with social engineering.
From Risky Biz News:
U.K. NCA “on its knees,” bleeding staff, seriously underpaid: A U.K. anti-corruption organization has published a report this week warning that the U.K.’s top police investigative body—the U.K. National Crime Agency (NCA)—is close to a critical collapse, describing its current state as “on its knees.” According to the Spotlight on Corruption, the NCA is dealing with huge staff turnover, recruitment issues, and chronically low pay. The study’s results are below:
- 9 percent of NCA roles are unfilled due to recruitment issues—more than double the average of 3.9 percent for the public sector and higher than the 4.8 percent in the voluntary sector.
- Despite a 7 percent pay award last year, NCA officers’ median pay has dropped by 16.3 percent in real terms since 2013–2014, when the agency was established. The proposed 5 percent pay award for this year still leaves officers with a 13.9 percent real-terms pay cut compared to over a decade ago.
- The NCA faces a major brain drain with a quarter of senior managers leaving annually, and the agency loses a third of its legal expertise annually.
- 59 percent of NCA officers are stuck at the bottom of their pay range with no chance of pay or career progression.
U.S. charges GRU cyber unit members: The U.S. government has charged five officers from a Russian military cyber unit involved in cyberattacks against Ukraine and NATO countries. Officials say the group launched the WhisperGate data-wiping malware ahead of Russia’s invasion of Ukraine. The malware destroyed Ukrainian government systems in an attempt to delay its response to Russian invasion forces. The five allegedly worked with a sixth suspect, a Russian civilian the Justice Department charged at the end of June. Officials say the five suspects are part of Unit 29155 in Russia’s GRU military intelligence agency. The unit is considered one of the GRU’s best and has also been involved in attempted coups, assassinations, and sabotage missions. The U.S. State Department is also offering a $10 million reward for information on the unit and its members.
Source: State Department Rewards for Justice post on X
Two security enhancements coming to Windows (ActiveX, CLFS): Microsoft announced last week two changes to its products designed to boost the company’s security posture. Redmond plans to disable ActiveX in Office apps in October and then harden the Windows Common Log File System (CLFS) logging service against logic bugs in future versions of Windows 11. Both are important steps that address some of today’s biggest attack surfaces in Windows.