U.K. Government To Consider Licensing Ransomware Payments

Published by The Lawfare Institute
in Cooperation With

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz
U.K. Government to Consider Licensing Ransomware Payments
The Record this week reports the U.K. government will propose a range of strong counter-ransomware measures, including mandatory reporting of all ransomware attacks, a licensing regime for payments, and a ransom payment ban for organizations involved in critical national infrastructure.
Multiple sources told The Record these proposals will be published in a public consultation next month. This may lead to new laws, but it is unlikely that they will arrive any time soon.
Despite recent law enforcement success against the LockBit ransomware gang, ransomware crime still causes extensive harm (see Change Healthcare in the U.S., for example). Governments still need to keep pulling levers to try to reduce the impact of these events.
Mandatory reporting of attacks and payments is a good idea with few downsides. It would furnish the government with the information it needs to better understand the size and scope of the problem and how best to respond. And as long as reporting thresholds are set appropriately, it would not be too onerous for businesses.
A licensing regime for ransomware payments is an interesting idea. This could be used to ensure victim firms explored other alternatives prior to making a payment, could make life more painful for ransomware-as-a-service operators by giving victim firms additional leverage in negotiations (“government says … no”), and could also ensure payments are made only when absolutely necessary.
It does come with potential downsides. If the licensing process was slow (and introducing friction is part of the point), it could delay recovery and exacerbate the disruption caused by a ransomware attack.
A ban on payments in critical infrastructure is intended to remove the incentive for ransomware gangs to attack those services. We previously examined arguments against banning ransomware payments and sense a bit of cognitive dissonance in this particular proposal. After all, if a ban is going to work, why limit it to just one sector? Why not implement it across all industries?
There are other measures that have been implemented elsewhere that we like. New York state’s financial services regulator, for example, requires firms above a certain size to:
- Notify DFS [New York State Department of Financial Services] within 24 hours of any extortion payment made; and
- Within 30 days of a payment, provide DFS with a written description of the reasons payment was necessary, alternatives to payment considered, diligence performed to find alternatives to payment and to ensure compliance with applicable regulations, including those of the Office of Foreign Assets Control.
This regulation came into force in December 2023 and could be seen as a compromise position compared to the immediate implementation of a payment licensing scheme. It should provide information that could be used to figure out whether a licensing regime is justified and necessary.
One real problem here is that the pace at which ransomware evolves in response to countermeasures is far faster than the legislative cycle. In the U.S., for example, legislation requiring critical infrastructure entities to report cybersecurity incidents (CIRCIA) was passed in 2022, yet regulations are still in draft form and likely won’t come into effect until 2026.
There are other options with quicker turnaround times, such as consultation with industry groups that have some influence. Last week, for example, the U.K.’s National Cyber Security Centre (NCSC) published guidance for ransomware victim firms that had been written with the assistance of the insurance industry.
The advice includes reviewing alternatives to ransom payments and notes that law enforcement sometimes has access to free decryption keys. Another suggestion is to record decision-making:
Maintaining a careful record of the incident response, decisions made, actions taken and data captured (or missing) is important for post-incident reviews, lessons learned or presenting evidence to a regulator. During an incident, it is sensible to record decision-making offline, or on systems that are not impacted by the incident.
In our view, this is the kind of information that should be analyzed by a regulator to inform best practices for other victims.
Even without strong sticks and carrots, there is still a lot that can be learned to improve overall responses—if government has the right information.
Evolving Threats to Democratic Processes Require Stronger Defenses
The U.K. government is ramping up efforts to protect politicians and other individuals in the political system from online threats. This is a good start, but as adversary cyber operations become more aggressive and even coercive, cybersecurity authorities need to do even more.
Last week, the U.K.’s National Cyber Security Centre (NCSC) announced its Personal Internet Protection service, an opt-in service designed to boost the online defenses of political candidates, election officials, and other people at high risk of being targeted online during an election year.
This service extends the U.K. government’s Protective DNS Service (PDNS) to these high-risk individuals. The PDNS has been operating since 2017 and is available to U.K. government organizations but hasn’t previously been made available to individuals.
The PDNS works by filtering DNS requests and preventing users from reaching malicious domains. A blocklist of these domains is created by the NCSC from internal, commercial, and open sources.
The Personal Internet Protection service is part of the NCSC’s “Defending Democracy” guidance, which it describes as “a wider package of cyber support on offer prior to the next general election.”
This guidance package includes tailored advice for individuals, bodies that organize elections, and political organizations. Individuals can also sign up for the NCSC’s account registration service, which will notify people if the NCSC learns of a cyber incident impacting a personal account.
The NCSC announcement of the Personal Internet Protection service cited government announcements about state-affiliated Russian and Chinese groups targeting U.K. institutions and individuals including parliamentarians.
This is all good stuff. But how much further should cybersecurity agencies be going?
There is lots of evidence that adversary states are targeting democratic processes in an expansive way. The Mueller report examining interference in the 2016 U.S. presidential election, for example, described Russian government efforts as “sweeping and systematic.” Russian cyber agencies targeted U.S. election infrastructure and both major political parties while other groups engaged in social media manipulation.
These wide-ranging campaigns give adversary states the opportunity to exploit the “seams or gaps” where democratic institutions are less well defended or more vulnerable. Despite extensive targeting of U.S. election infrastructure (the vote-counting apparatus), ultimately Russian cyber efforts didn’t try to interfere with the vote count and instead focused on social media manipulation and the public disclosure of hacked materials.
There are reasons to think the political class is one of those points of vulnerability. In a survey, Australian parliamentarians rated political parties, state and local governments, and political representative’s offices as the least “cyber resilient” actors. (Cyber resilience was defined as how well an organization or individual could manage a cyberattack or breach.)
In the same survey, despite identifying themselves as some of the least resilient actors, parliamentarians prioritized critical infrastructure when it came to investment. That’s entirely justifiable but at the same time means that politicians, their staff, and other political entities are likely to remain relatively vulnerable. They will likely remain one of the “seams” that will be targeted by adversary countries.
It’s not just Russia that engages in this kind of political targeting, either. In March, the U.K. government publicly outed two China state-affiliated campaigns targeting “democratic institutions and parliamentarians.” One campaign breached the U.K.’s Electoral Commission systems and another targeted parliamentarians.
The campaign targeting parliamentarians also affected at least six Australian legislators, members of the transnational Inter-Parliamentary Alliance on China (IPAC).
The legislator’s announcement about the incident earlier this month notes that “we were not informed by Australian agencies … about this targeting.” The announcement also says the affected politicians have “received an assurance that agencies will inform members of Parliament (MPs) about future attempts to target them, particularly by state sponsored groups.”
The Nightly reports the attempted attacks took place in January 2021 and that the Australian Signals Directorate (ASD) was warned of them in mid-2021. The report says ASD decided not to tell the parliamentarians about the spear phishing attempts because they were crude and the organization had confirmed they were unsuccessful. In addition, MPs and the public were already being warned to improve their cybersecurity.
That reasoning made sense in a world where cyber operations were solely about intelligence collection and were kept secret by default. That world doesn’t exist any more. The spear phishing could well have been a part of a broader operation to damage IPAC’s reputation and diminish its influence. Being forewarned would have been valuable.
In our view, elevated threat levels require a more proactive response from cybersecurity authorities. Offering technical defenses like the U.K.’s Personal Protective Service to a broader group of at-risk individuals should be just the first step.
Three Reasons to Be Cheerful This Week:
Incognito dark market operator arrested: U.S. authorities have arrested a Taiwanese national, Rui-Siang Lin, for allegedly running the Incognito dark web marketplace. Incognito Market was an online narcotics bazaar, and the U.S. Department of Justice says it has sold over $100 million since its creation in October 2020. Lin was arrested in New York, just months after he shut down the site and attempted to extort users by threatening to publish their data.
Movement on improving BGP standards: The U.S. Federal Communications Commission (FCC) has proposed new rules that will require U.S. telecommunication companies to file confidential reports on BGP security incidents. There is no shortage of BGP mistakes or deliberate hijacks, and China Telecom has been accused of using the technique to intercept U.S. domestic internet traffic.
EPA steps up cybersecurity warnings: The U.S. Environmental Protection Agency (EPA) has warned that it will launch enforcement actions against “community water systems” if they aren’t meeting their obligations under the 2013 Safe Drinking Water Act. The good news is that the EPA is trying to improve standards. However, the bad news is that from a cybersecurity perspective these obligations are quite limited. The act requires that these water systems create and regularly update risk assessments and emergency response plans that include cyber threats. But they don’t spell out any concrete security measures that must be implemented.
Shorts
Google Puts Boot Into Microsoft’s Security Failings
A Google blog post has highlighted its own security efforts while pummeling Microsoft’s security record. Although the post doesn’t refer to Microsoft by name, it celebrates a recent Cyber Safety Review Board (CSRB) report into the 2022 breach of Exchange Online by Chinese state-sponsored actors. Google says the report shows “that lack of a strong commitment to security creates preventable errors and serious breaches.” This is undoubtedly self-serving, but it is still great to see more examples of technology companies using security as a basis for competition.
Apple’s Geolocation System Privacy Booboo
Krebs on Security has a fascinating article about how Apple’s WiFi-based positioning system can be used to map previously unknown wireless access points across the entire world. Researchers say this included the location of Starlink terminals in conflict areas such as Ukraine (Starlink has issued a fix after being contacted by the researchers). Ironically, it appears that Apple’s bias toward on-device processing (which it argues is more private) inadvertently makes the service vulnerable to this kind of global mapping.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq continue part II of their discussion about what it takes to be a cyber power and look at how countries leverage companies.
From Risky Biz News:
Feds seize BreachForums again: Five days after a threat actor advertised Europol stolen data on a hacking forum, law enforcement agencies moved to seize the site.
Agencies from the U.S., the U.K., Australia, New Zealand, Switzerland, and Iceland took down the second incarnation of BreachForums, a well-known hacking forum where threat actors went to sell, buy, and leak hacked data. The takedown took place on May 15 and comes more than a year after authorities took down the site’s first version in March 2023. At the time of this newsletter, there is no formal announcement on the takedown, and it’s unclear if any arrests took place.
Authorities took over the forum’s official website and its Telegram channel. In a message left on Telegram, authorities claim they’re now in possession of the site’s backend database, which they plan to analyze for further criminal activity.
[more on Risky Business News]
DNSBomb attack is here! Pew pew pew!!! A team of academics from Tsinghua University in Beijing, China, has discovered a new method of launching large-scale DDoS attacks using DNS traffic. The new attack is named DNSBomb and is a variation of a 2003 paper that described a DDoS attack technique using TCP pulses. The DNSBomb attack works by sending a slow trickle of modified DNS requests to DNS servers, which bounce the data around, amplify its packet size, and withhold it to release everything at once in a pulse of DNS traffic aimed at a target.
[more on Risky Business News, including how the attack works, the services affected, and remediation steps that have been taken]
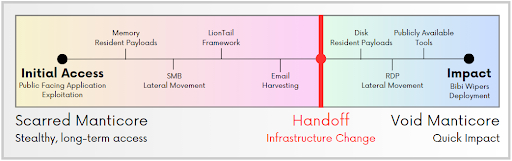
Iranian APT handoffs: Check Point says that two Iranian APT groups have collaborated in attacks carried out over the past several years against targets in Albania and Israel. The first group, named Scarred Manticore (Storm-0861), breaches the intended targets and hands off access to a second group named Void Manticore (Storm-0842). The first group is focused on intelligence collection, while the second group deploys ransomware and data wipers and leaks data as part of information and influence operations. Check Point says both groups are affiliated with Iran’s Ministry of Intelligence and Security (MOIS) and are using what appears to be a well-documented handoff procedure, suggesting a consistent level of planning of attacks between the two.
Disclosure: Google provides financial support to Lawfare. This newsletter was submitted and handled independently through Lawfare’s standard editorial process.


.png?sfvrsn=4156d4f8_5)
-(1)-(1).png?sfvrsn=1bc11cd_4)

