-
The Cybersecurity Information Sharing Act of 2015 passed out of the Intelligence Committee by a 14-1 vote. With that passage, and the House adopton of two similar bills in April, some of us had begun t...
-
Willy Stern has a very interesting essay at the Weekly Standard about “Dabla,” the Israeli Defense Force’s elite operational lawyers.
-
Critical attention to the Obama Administration’s handling of the ongoing conflict with al Qaeda and associated forces tends to center on debates over drones and targeted killing, not captures. This may b...
-
Published by Oxford University Press, 2009
-
International Criminal Court preparing to send an investigative team to Israel: The Israeli daily Haaretz reports that the ICC’s Prosecutor’s office is preparing to send a team to Israel as parts of its ...
-
The Obama administration plans to send up to 450 additional US troops to Iraq to assist in the fight against ISIS--a decision likely influenced by the recent fall of Ramadi. Josh Earnest, the White House...
-
First, there was the "drone strike cake," called "notorious" by Rolling Stone Magazine.
Then there was the "Zero Dark Thirtieth Birthday Cake," because, well, . . . just because.
Now, the mysterious an...
-
Our guest for Episode 70 of the Cyberlaw Podcast is Dan Kaminsky, a famous cybersecurity researcher who found and helped fix a DNS security flaw.
-
On Monday, the Special Representative and head of the United Nations Support Mission in Libya (UNSMIL), Bernardino León, presented a new draft political agreement for Libya at a meeting of the Libyan Pol...
-
As the United States reigns in its surveillance practices, France is expanding its own.
-
The Harvard National Security Journal’s spring issue, published last week, may be of interest to readers of Lawfare. It has four major articles. Antonia Chayes previews her forthcoming book, Borderles...
-
Much anticipated for any number of reasons, Zivotofsky was perhaps most awaited for the valuable contribution it was to make in the form of its analysis of the scope of exclusive executive power. This an...
-
A year ago, U.S. policy on zero-day software flaws—vulnerabilities unknown to software vendors or users—made headlines. Now, zero-days are back in the news: on May 20, 2015, the U.S.
-
Mike Schmitt is well-known to many, probably most, regular readers of Lawfare—eminent and prolific scholar of the law of armed conflict (or international humanitarian law); driving force behind the Talli...
-
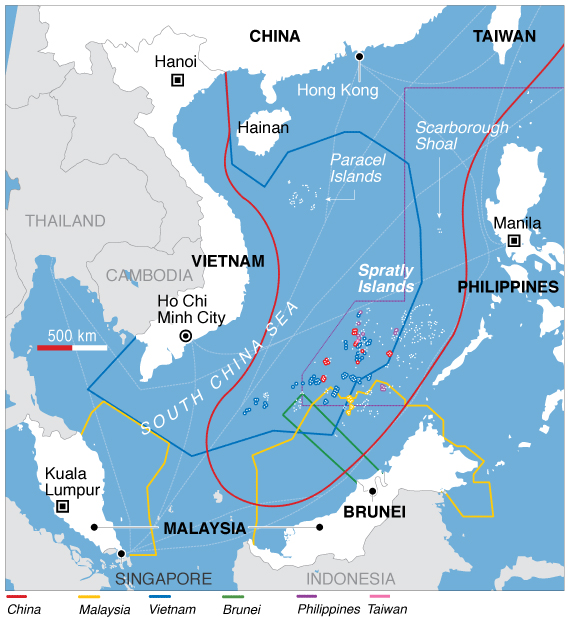
Although the United States will often urge the claimants to resolve the South China Sea dispute in accordance with “international law” writ broadly, the conflict is governed in reality by a number of dif...
-
On June 5, 2015, in connection with recent motions practice, attorneys for habeas petitioner Mukhtar Yahia Naji al Warafi filed a supplemental memorandum with the U.S. District Court for the District of ...
-
According to the Pentagon, Iraqi security forces have demonstrated progress in their efforts to maintain control of the oil refinery outside the northern Iraqi city of Baiji. The Wall Street Journal repo...
-
The United States is in the midst of a transition that will, when completed, give up its contractual control of the Internet Assigned Numbers Authority (IANA). That authority is currently conducted by t...
-
It was a little dizzying this morning to read the NYT editorial board's full-throated endorsement of the Court’s decision in Zivotofsky.
-
Last year the Supreme Court, seized with a big constitutional question about foreign relations, feinted: Bond v. United States turned on rules of statutory interpretation rather than the constitutional b...





























.jpg?sfvrsn=d0f071b6_5)

